With wireless technology, without using cables or wires, we can transfer data or communicate from one point to another point efficiently. Wireless technology has evolved tremendously over the years. New technologies are emerging in the world, such as robots, drones, self-driven vehicles, and new medical devices, which is the need for the Internet of Things (IoT). In this article, we will look at some current wireless technologies and how they will change how people and organizations communicate in the future. These trends may arise from organizations’ need to be more agile in responding to market and customer demands, data security concerns, and the Internet of Things.
Top 10 Wireless Technology Trends
- 5G Cellular
- Wi-Fi
- Wireless Sensing
- Low power wide area (LPWA) networks
- Evolution toward IoT (Internet of Things) connectivity
- Millimetre wave wireless
- Space exploration and tourism
- Network automation
- Vehicle to everything (V2X) wireless
- Software defined radio(SDR)
1. 5g Cellular
5G cellular technology has supplemented Wi-Fi technology as a hugely cost-effective and high-speed information networking solution at significant sites such as ports, airports, and factories. Currently, 5G is in the development stage, and complete development and upgrading would take five to eight years. Currently, most suppliers focus solely on selling 5G as high-speed broadband. However, 5G may eventually bring improvements in the areas of the Internet of Things (IoT) or just low latency applications.
5G speeds can range from 50 to 1,000 Mbit/s (1 Gbit/s). The fastest 5G speeds would be in the mm-wave bands, where carrier aggregation and MIMO could achieve 4 Gbit/s. Sub-6 GHz 5G (mid-band 5G), far and away from the most common, can typically deliver between 100 and 4,400 MBits/s.
- However, it can reach much more than millimeter waves, particularly outdoors. The C-Band will be deployed by numerous U.S. operators in 2022.
- 5G is intended to deliver peak information rates of up to 20 Gbps. But 5G is concerned with how fast it is. In addition to higher peak information rates, 5G is intended to supply more network capability by increasing into a spectrum like an mm
- 5G may even provide abundant lower latency for a more immediate response, as well as more uniform user expertise so that information rates remain consistently high even when users are in
- In addition, the new 5G NR mobile network is protected by a Gigabit LTE coverage foundation, which may provide current Gigabit-class
- 5G, like 4G LTE, is OFDM-based (Orthogonal frequency-division multiplexing) and can operate on an equivalent mobile networking
- However, theology for homes as well as offices, Wi-Fi can have new domains to support, like microwave radar systems, suggesting two-issue authentication
- Wi-Fi has been around for a long time and is expected to remain the primary efficient networking technology for homes and offices until
- Beyond simple communications, Wi-Fi can take on new roles “for example, in measuring device systems or as a component in two-factor authentication.”

2. Wifi
How does Wi-Fi work? WiFi uses radio waves to transmit data from the wireless router to Wi-Fi-enabled devices such as your TV, smartphone, tablet, and
- Your devices and personal information will be vulnerable to hackers, cyber-attacks, and other threats because they communicate over the airwaves. This is particularly true once you connect to a public Wi-Fi network at places like a restaurant or landing field. Attaching to a password-protected wireless network or a private hotspot is best when possible.
- A wireless access point (AP) lets wireless devices connect to the wireless network. Having a wireless network makes it simple to bring new devices online and provides versatile support for mobile
- Whatever is done by the wireless access point for your network is similar to whatever is done by the electronic equipment for your home
- An access point stretches the bandwidth returned from a router so that several devices can continue the network from a greater distance
- But a wireless access point will simply extend Wi-Fi. It may also provide helpful knowledge regarding the devices on the network, provide proactive security, and serve differently sensible
- A mobile hotspot may be a standard feature on smartphones with tethered and untethered
- When you activate your phone’s mobile hotspot, you share your wireless network connection with other devices, allowing them to access the
- A portable Wi-Fi hotspot may be obtained through a cellular phone carrier. It is a tiny device that uses cellular towers to broadcast high-speed 3G or 4G broadband signals.
- Multiple devices, like iPads and laptops, will then connect wirelessly to the device, which in turn seamlessly connects to the web wherever you
- Similar to a telephone, the portable hotspot’s monthly price is predicated on the information usage set-up you
- A portable Wi-Fi hotspot could be a lot more reliable way to access the net than finding out-of-status public Wi-Fi
3. Wireless Sensing
The primary purpose of sensing is the absorption of signals and reflecting them. This sensing technology could also be used for indoor radio detection and guidance systems for robots and drones. Virtual assistants can use measuring and chase systems to spice up their performance once several people talk in one area.
Information from a device powers IoT systems and is used in various applications such as medical nosology, beholding, and intelligent home interactions. The absorption and reflection of wireless signals could also be used for sensing functions. Wireless sensing technology is often used, for instance, as an inside measuring system for robots and drones.
- Virtual assistants can also use measuring systems to boost their performance once multiple people’s area units speak inside an equivalent area. Device information is the fuel of the IoT. Consequently, new device technologies enable innovative kinds of applications and
- Systems containing wireless sensing are going to be integrated into a multitude of use cases, ranging from medical medicine to beholding and intelligent home
- The design and applications of wirelessly networked and embedded sensors have advanced dramatically in recent
- Wireless device nodes are typically low-cost, low-power devices with limited sensing, processing, and wireless communication capabilities, as well as limited
- They make use of the concept of wireless device networks (WSNs), in which a large (possibly massive) number of cooperative device nodes are frequently
- As a result of the convergence of micro-electromechanical systems (MEMS) technology, wireless communications, and digital, and physical science, WSNs represent a significant improvement over traditional
- In fact, the rapid evolution of WSN technology has accelerated the emergence and development of various novel types of wireless sensors, such as multimedia
- Sensors and devices used in wireless device networks are cutting-edge technology at the lowest possible cost, so the measurements we get from these devices are frequently strident, incomplete, and inaccurate.
- Researchers learning about wireless device networks suppose that rather a lot of knowledge could also be extracted from several unreliable measurements unfolding across a field of interest than from a smaller variety of high-quality, high-reliability instruments with constant total
- Matt Welsh gave a term known as micro-programming, which refers to programming the entire detector network as an academic degree ensemble rather than individual detector nodes. A network is to appear on the device network as information resulting from the macro-program.
4. Low Power Wide Area (LPWA) Network
LPWA (sometimes known as mobile IoT) networking technologies, like LTE-M and NB-IoT, transmit knowledge at slower rates than different cellular technologies. However, LPWA technologies also cost less, use less power, have higher wireless coverage within buildings, underground, and rural areas, and may transmit information to additional devices in a condensed space than these alternative cellular technologies—low bandwidth property for IoT applications in an other power-efficient mode to support an extended battery life.
Low power wide area networks like Narrowed Band IoT (NB-IoT), long-term evolution for machines (LTE-M), LoRa, and Sigfox cover massive areas like big cities or countries. Comparatively, cheap modules let IoT makers enable small, low-cost, battery-powered devices like sensors and trackers.
- At that time, the marketplace for connected things was small and principally dominated by personal area network (PAN) technologies, like Bluetooth, and wireless local area network (WLAN) technologies, like Wi-Fi.
- With all of the hype surrounding the Internet of Things, several analysts predicted there would be more than twenty billion connected devices. Most of this volume was expected to go to PAN/WLAN technologies, not to ancient cellular.
- That’s a result of PAN and WLAN technologies excellently meeting the price and power needs of IoT applications.
- However, these technologies offer very little coverage, which is the critical demand for several IoT
- Even with its superior coverage, ancient cellular still has dead zones deep within buildings or in remote
- LPWAN technology enables IoT devices to operate reliably for up to ten years on a single
- This period is ideal for solutions with limited mobility that lack a reliable power supply for charging, such as smart meters, intelligent towns, track and trace, smart agriculture, and intelligent building applications.
- LPWAN technology allows for information transfer in the form of small, intermittent data packets ranging in size from ten to a thousand
- This permits improved potency and optimized speeds starting from three Kbps to 375
- Because LPWA networks operate with higher power and bandwidth efficiency and over an extensive area, less infrastructure and hardware are required. These options translate into higher value
5. Evolution Toward IoT Connectivity
As we evolve towards IoT connectivity or the Internet of Things, many more devices and appliances are connected wirelessly through the web. This may be an enormous game-changer in five years’ time because it means our machines can currently tell us when they are running low on supplies, would like maintenance, or have been damaged. These devices will also be able to tell us how typically they have been used and for what period, which implies customers will have much better control over their energy consumption.
IoT design:
- The definition of IoT reveals that any IoT system includes things or devices that generate information, a network that transmits information, and services that store and process this information. An IoT system will be said to possess these three layers:
- an application layer
- an edge computing layer
- and a physical
- Over the last few years, the Internet of Things has seen tremendous
- This is primarily due to advancements in three technologies: cloud computing, big data, and artificial intelligence. The availability of low-cost storage in the cloud has enabled businesses to store the large amounts of information generated by IoT systems at reasonable
- Big data technologies have made it easier to organize and use the data generated by IoT systems. Artificial Intelligence and its associated technologies have enabled the generation of insights that facilitate business
- Because IoT has a longer lifespan will be more innovative and revolutionary than current technologies. That more and more domains will embrace IoT may be a foregone 5G integration:
- 2020 has already seen testing of 5G by several firms. IoT design will be integrating 5G into systems, both new and
- 5G would vastly improve the capabilities of existing networks; 5G would not replace, but rather enhance, the current Multi-level privacy and security:
- Security and data privacy are paramount. Historically, data security has been enforced at the device level, be it a smartphone, a laptop, or other smart device connected to the IoT network.
- Although a range of industries and businesses is adopting IoT, there are multiple challenges in its
- Data is an essential component of any IoT system. So that the business is not overwhelmed by an excessive amount of data; only the desired data is
- The collected data should then be stored and transmitted in a highly secure manner so that neither the users nor the IoT devices are
- The rise of the IoT has been supported by advancements in three technologies: cloud computing, big data, and AI. The future of IoT looks promising. 5G is about to disrupt the IoT in a massive manner by providing high-speed transmission capabilities to existing and new IoT networks.
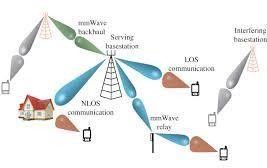
6. Millimetre Wave Wireless
A millimeter wave (MM wave), also referred to as the millimeter band, is the band of the spectrum with wavelengths between 10 mms (30 GHz) and 1 millimeter (300 GHz). It’s also referred to as the extraordinarily high frequency (EHF). They operate at 30 to 300 gigahertz frequencies, with wavelengths within the 1 to 10 millimeters range. This technology will be utilized by wireless systems like Wi-Fi, short-range 5G, and high bandwidth communications like 4K and 8K video streaming. A millimeter wave is a band of the electromagnetic spectrum that may be used in various products and services, like high-speed, point-to-point wireless local area networks (WLANs) and broadband access. In telecommunications, millimeter waves are employed for multiple services on mobile and wireless networks because they allow higher information rates than at lower frequencies, like those used for Wi-Fi and current cellular networks. Propagation restrictions propose using tiny cell sizes for Wi-Fi and cellular networks. The short propagation distance increases the number of access points (APs) that can be used to cover a large area, but it also means fewer consumer devices can share the bandwidth in each cell. Small cells also make using channels across the (WLAN) wireless local area network (wireless fidelity coverage area) easier. Millimeter wave antennas are smaller than those used for other frequencies, making them ideal for small Internet of Things (IoT) devices.
- Millimeter waves are used in various applications, including telecommunications, short-range radar, and airport security scanners.
- The high bandwidth is ideal for short-distance wireless transmission of ultra-high definition video and communications from small, low-power Internet of Things devices.
- Because of the short propagation distance, small cell size, and high information rates, millimeter waves are ideal for communication between autonomous vehicles. On the other hand, Wi-Fi currently uses frequencies in the 2.4 GHz, 5 GHz, and 6 GHz bands, known as microwave bands. , cellular networks use frequencies within the 600 MHz to 700 MHz and 5 GHz to 3.7 GHz rate bands.
- These bands propagate farther than a millimeter wave but support lower bandwidths. Frequencies higher than millimeter waves are within the low spectrum and limited to short, line-of-sight communications.
- In contrast to higher frequency ultraviolet, X-ray, and gamma radiation, mm-wave radiation is non-ionizing.
- Their studies focused on heating the eyes and skin, which is caused by the absorption of those waves. So far, there hasn’t been a lot of research done on millimeter waves and their health effects.
- Millimetre waves have a shallow penetration depth and are only deposited in the first 1-2 millimeters of human skin. Because of this, they need to be used for plenty of therapies and health-related
- Millimeter waves free up more spectrum and relieve congestion in the existing radio spectrum. Today, several electronic elements can operate in millimeter waves, so the millimeter wave spectrum remains
- However, this spectrum faces many challenges and is an obstacle for many industry players. The major challenge has been media movement due to poor penetration due to atmospherical and free-space paths. Millimeter waves face challenges such as part absorption, free area loss, and signal scattering due to rain.
7. Space Exploration And Tourism
Space exploration is expected to remain a thriving industry in the coming years, with more and more countries preparing to launch their space programs and establish off-world colonies. A company referred to as SpaceX plans to place 1 million individuals on Mars by 2050. So, although progress might not be as quick as Elon Musk would like, we are undoubtedly headed in the right direction.
- In terms of space tourism, it won’t be too long before you can travel into space for a vacation. So, as part of this work, a vast system of satellites has to be
- These satellites can be “net gateways” to transfer information packets. Each piece of hardware can have its IPN address or Mars domain name. They’ll serve as nodes in operation on a packet-switched
- Some major potential issues include lag, weak signal, and reduced bandwidth. The answer to any or all of those lies in a new IPN protocol being
- This protocol and high-precision instrumentality can facilitate eliminating all of those. The protocol has been modified from our TCP/IP protocol in two significant ways.
- This preliminary could be a packet delivery scheme that does not clog the system by re-sending missing packets. Therefore, IPN instead keeps track of inbound parcels and requests missing ones at the tip of
- The second limitation is that packet headers only use one-tenth of the maximum bandwidth available to TCP/IP. Back on earth, there’ll be gateways to
- Secure communications are projected using a laser N-slit interferometer, where the laser signal takes the shape of an interferometer-type pattern, and any attempt to intercept the signal causes the interferometric way to
- This technique uses populations of indistinguishable photons and has been proven to figure over practical propagation distances, and, in theory, it can be applied over giant distances in
- The variation for satellite-to-satellite communications is around 2,000 km (1,200 mi), assuming available laser technology and accounting for interferometric signal divergence. These estimates apply to an array of satellites orbiting the
- For spacecraft or space stations, various communication channels with ranges of up to 10,000 km (6,200 mi) can be calculated. Laser Focus World selected this approach to secure space-to-space communications as one of the top photon developments of

8. Network Automation
Network automation could be a methodology within which software automatically configures, provisions, manages, and tests network devices. Enterprises and service providers use it to enhance potency, decrease human error, and lower operating costs. Network automation tools support functions starting from basic network mapping and device discovery to additionally complicated workflows, like network configuration management and the provisioning of virtual network resources. Network automation additionally plays a crucial role in software-defined networking (SDN), network virtualization, and network orchestration, sanctioning the automatic provisioning of virtual network tenants and functions like virtual load balancing.
- Network automation is similar to software programming in that it manages and schedules the automation of various tasks using similar logic and
- To program network automation, common “if X, then Y” call statements are
- Popular SDN platforms employ a centralized management plane and, on occasion, previously used and rebuilt automation tasks that will be adjusted and scheduled. • Alternatively, network groups will use external tools to create scripts executed via a command-line interface (CLI) or application programming interface (API).
- Examples of everyday network automation tasks used in production environments include: bandwidth forecasting for web and WAN links; network and device inventory and monitoring; service-level agreement observing and alerting; automated network configuration backups; massive configuration results in changes to different networks and clouds; and access port turn-ups and turn-downs based on a worker onboarding and off-boarding
- Network device incompatibility:
- several legacy network devices are secured into proprietary ecosystems and can’t tap into APIs. Additionally, this limits the categories of automation tools used because of the effectiveness of network automation capabilities.
- Tool complexity:
- Automation tools will produce additional complexes, particularly once AI and machine learning are added to the combination.
- Hybrid and multi-cloud environments that are incompatible with some automation tools will hinder the potency
- Network automation is one of the critical methodologies supporting the evolution of intent-based networking and network validation.
- These concepts make use of software systems to map how enterprises will harness their resources to meet the business demands that their networks must
- Automation is progressively enabled through a graphical user interface (GUI). Engineers use a graphical user interface to determine how their network operations should run to satisfy a specific objective.
- Regardless of the marketer, a graphical user interface will then automatically run configuration and different management changes made to the network
- In automation, AI and machine learning tools are frequently used to investigate networks, recommend troubleshooting steps, and validate network

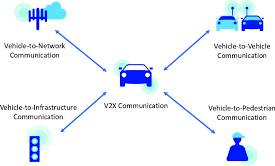
9. Vehicle To Everything (V2X) Wireless
Vehicle to Everything (V2X) may be a transport communication system that supports data transfer from a vehicle to moving components of the traffic system that will affect the vehicle. The vital purpose of V2X technology is to increase road safety, energy savings, and traffic efficiency on the roads. In a V2X communication system, the data travels from the vehicle sensors and alternative sources through high-bandwidth, high-reliability links, permitting it to communicate with different cars, infrastructure like parking areas and traffic lights, and smartphone-tossing pedestrians.
- By sharing data, like speed, with alternative entities around the vehicle, the technology improves the driver’s awareness of potential dangers and helps decrease the severity of injuries, road accident fatalities, and collisions with different
- The technology also enhances traffic potency by warning drivers of approaching traffic, suggesting various routes to avoid traffic, and distinguishing parking Elements of V2X Technology:
- The key elements of V2X technology include V2V (vehicle-to- vehicle) and V2I (vehicle-to-infrastructure).
- V2V allows vehicles to communicate with other cars on the road, whereas V2I will enable vehicles to share with external entities such as traffic lights, parking lots, cyclists, and pedestrians.
- The technologies improve road safety, reduce fuel consumption, and improve communication between drivers and other road users like cyclists and
- When V2X systems are integrated into ancient vehicles, drivers close to receiving necessary data regarding the weather patterns, near accidents, road conditions, road works warnings, an emergency vehicle approaching, and activities of different drivers using identical
- Autonomous vehicles equipped with V2X systems might offer additional data to the present navigation system of the car. The plans also make it possible for autonomous vehicles to scan the surrounding atmosphere and make immediate selections based on the data
- The automotive trade has been operating with regulative bodies to standardize V2X
- The goal is to ensure that all stakeholders manage the ability to control the power between vehicle brands as well as the road infrastructure to induce standardized
- In most countries, governments take V2X technology into account as an essential factor in reducing road fatalities. As a result, they’re pushing the trade to shorten the preparation schedule for the technology for car manufacturers and many more.
10. Software-defined Radio
A software-defined radio (SDR) could be a radio communication system that employs re-configurable software-based parts for the processing and conversion of digital signals. In contrast to traditional radio communication systems, these radio devices are highly flexible and versatile. This could be an emerging technology used to connect our ever-increasing wireless world. SDR shifts the bulk of the signal processing in a radio system away from chips and into software. This permits the radio to support more frequencies and protocols. The technology has been accessible for several years but has never taken off because it is costlier than dedicated chips. However, SDR will grow in quality as new protocols emerge. As older protocols are rarely retired, SDR will modify a device to support legacy protocols, with new protocols simply being enabled via software upgrade.
- The front end of an SDR system processes signals in the analog domain, whereas the back end processes signal in the digital environment. Analog-to-digital (ADC) and digital-to-analog (DAC) converters are used to convert signals between
- The digital back-end options a field-programmable gate array (FPGA) and utilizes configurable logic gates for various functions. This FPGA has numerous aboard digital process capabilities and modulation, demodulation, upconversion, and down-conversion. Because this digital back-end is reconfigurable, new algorithms and protocols can be implemented without modifying the existing hardware.
- The flexibility of the SDRs makes them an appropriate choice for a broad array of markets. This includes numerous crucial applications like radar, test and measurement, magnetic resonance imaging (MRI), global navigation satellite systems (GNSS), low latency links, and spectrum and
- The design of a typical SDR platform consists of the following boards: power, digital, time, receive (Rx), and transmit (Tx) modules.
- The boards are linked with high-speed cables to ensure that information is transferred quickly from one panel to The function of the power board is to provide power to the daughter boards of an SDR system.
- Today’s SDR, in distinction, could be a general device in which a similar radio tuner and processors are used to implement several waveforms at several frequencies. The advantage of this approach is that the instrumentality is more versatile and cost-
- In addition, it may also be upgraded with a new software system for new waveforms and applications upon sale, delivery, and installation. Following the programmable electronic equipment, the Air Force Research Laboratory and the Defence Advanced Research Projects Agency joined forces to fund the Speakeasy-I and Speakeasy-II programs.
- Speakeasy-I was a six-foot tall device that was not portable in any way, but it demonstrated that an all software system programmable radio could be developed and enclosed as a software system programmable cryptography chip called Cypress, designed by the Motorola electronics
- Speakeasy-II was a radio the size of a stack of two pizza boxes, as well as the primary SDR to include a programmable voice computer programmer and enough electronic signal processing resources to handle a wide range of wave
- And these Speakeasy-II and DMR products evolved not only to outline these radio waveform features in software systems but additionally to develop an effective software system design to modify porting the software system to an arbitrary hardware unit and, therefore to conclude that hardware independence of the waveform software system.



















