Network Security
Hi,
My roommate and I share the same connection, via a wireless router. He was letting me see how he can see all the data coming in and out, the messages that I have been sending out through instant messaging were also there, which was ok at the moment.
For secured websites he couldn’t see anything only the IP address. I would like to have some privacy, would that be possible?
How?
- 1839 views
- 2 answers
- 1 votes
I am using one Windows 2007 server for the clients company. Last week till today morning, I put on the server and many users were accessing the server. Suddenly today, when I tried to open the server remotely, it’s showing, "network path not found”.
I got shocked to see the error, is there anyone help me in solving the issue?
- 1149 views
- 1 answers
- 0 votes
Hi,
Whenever I use the internet, my computer always gives me a notification that I am having an IP conflict. I am the only one using the network, as it is a private/personal DSL. I am using a Linksys Router.
I contacted my ISP and told them about the situation. They said that, there is a possibility that someone is trying to access my network illegally. Is that possible? My network is secure and my password is a bit difficult to manipulate.
If this helps, I also checked and my remote administration is disabled.
Anyway, just to keep it safe, I tried to change the settings and password, but nothing is happening. I followed all their instructions, but everything seems to be coming back to the previous setting.
- 6352 views
- 2 answers
- 1 votes
Hi,
How one can detect network "sniffer"? Is it designed to collect data that is flowing across a network.?
The data can be useful for many purposes, including troubleshooting, network traffic analysis, and security purposes. However, the data can be used for illegitimate purposes, such as a network attack.
This type of data can also be used for illegitimate purposes, including data theft, unauthorized access on passwords, and networking mapping (reconnaissance).
This type of passive network attack can be difficult to detect.
Thanks.
- 1226 views
- 2 answers
- 20 votes
Hi folks,
I installed Check Point VPN-1/FireWall-1 FP3 and later wanted to Check Point VPN-1 Firewall-1, to allow remote VPN client to access the protected resources behind the firewall.
The initial stages went on smoothly as I was able create network objects, configured user for remote access, configured the firewall object. But the problem arose when I tried to create a certificate. After clicking the Certificates tab, the certificate state reads, "there is no certificate for this object”. So I clicked on generate and then the save button, which gave me the error;
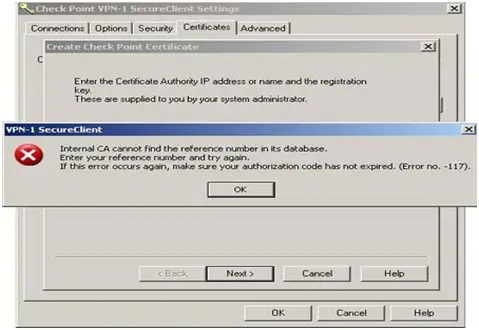
“VPN-1 Secure Client
- 1516 views
- 1 answers
- 20 votes
I want to setup a domain log in on my own office network with ten computers.
I want to remotely control or access each of those computers.
Do I need to turn off the Antivirus software to remotely access the computer?
I'd like to know also what is the best operating system I can use.
Can I use different Operating System on each computer?
Do I need to use a specific software or hardware to setup domain log in?
Can I access those computers at different locations, like outside the office?
And lastly, do I need high speed Internet do that?
- 1151 views
- 2 answers
- 21 votes
I am working as an assistant Engineer, system support department in a company.
Sometimes, I guess that someone’s accessing my desktop remotely via third-party software. It seems to me that the person is my boss. But I want to monitor or see the date and time, when he accesses my desktop? I also want an alert when he enters my desktop?
Is there any software that can give me a log file, of anyone gaining access my desktop remotely? And give me an alert, when someone is attempting to access my desktop? Or some tips that help me to do that. It is our company policy, that I can’t turn on my Windows firewall or any others firewall.
My Computer O/S is Windows Server 2003 and Windows 7.
- 2146 views
- 2 answers
- 24 votes
Do I need to set a banner in CISCO Networking configuration? I have to configure a router to make sure, that this configuration, will not be taken from other networks, that will try to access my network system illegally. Can you help me with this problem?
- 974 views
- 2 answers
- 23 votes
Dear All,
I'm working in a AD firm and using CISCO switch for our network. Recently we have purchased Cisco 2960 series switch. I’ve tried myself to assign static IP on switch but failed. For your information we are using Mac address. Is there anyone to instruct me, how can I can assign IP address in Cisco switch?
Regards,
Hossain
- 4507 views
- 7 answers
- 14 votes
I'm working in an AD firm and using CISCO switch for our network. Recently we have purchased Cisco 2960 series switch. I’ve tried myself to assign static IP on switch but failed. For your information we are using Mac address. Is there anyone to instruct me, how can I assign IP address in Cisco switch?
Regards,
Hossain
- 1835 views
- 7 answers
- 11 votes











