Uses and functionality of Wireshark
What is Wireshark
Wireshark is a free open source packet (network protocol) analyzer- the most popular in the world. Basically, what Wireshark does is that it captures all information related to network activity from a computer.

This information can then be used to perform important actions like troubleshooting and diagnosing any network performance difficulties. It was originally known as Ethereal until 2006 when the name was changed to Wireshark.
Why is this used
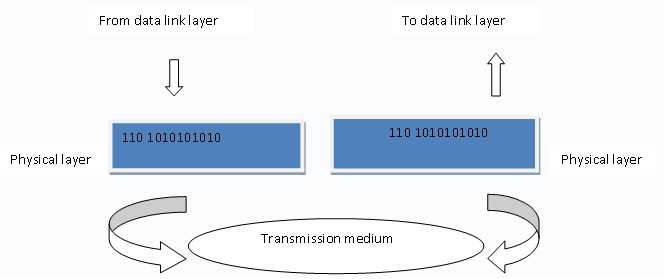
To understand why Wireshark is used, one needs to understand what exactly a network analyzer does. Essentially a network analyzer is a tool that “sees” the bits and bytes passing through a network in a form that can be read by humans. Another important fact worth understanding is that a network protocol is made up of 7 layers in a layer model known as the OSI7. Of these seven layers that the network protocol is broken down into, Wireshark interacts with six-from layer 2 to 7. This means that Wireshark can actually decode most of the protocols.
It is the ability to capture crucial network traffic that provides the basis for using Wireshark. Since network users need to know what is going on in their networks, they need a tool that makes it easier to achieve this goal and Wireshark does exactly this, it makes it possible for one to learn the activities of network protocols by seeing them in real-time.
Let us imagine you want to get a clear picture of how a certain protocol works, say the TCP protocol for example. Wireshark will capture traffic from the computer you are using to access the website and convert it into a trace file where you will now be able to view the fine details of the communication exchange for the protocol. Once you are able to view these details, it becomes easier to identify and solve a series of problems occurring in the network.
History of Wireshark
Around late 1997 a graduate of computer science from the University of Missouri-Kansas City by the name Gerald Combs started writing Ethereal, a program to track down network programs in a small ISP company where he was working. In 1998 July, version 0.2.0 of Ethereal was released and it received almost instant recognition because there was feedback and encouragement within a few days after its release-this formed the basis for its success. Given its promising success, Gilbert Ramirez figured out its possible potential and decided to give the program a boost by contributing low scale dissectors (drivers) to Ethereal.
This was followed by more contribution from Network Appliance’s Guy Harris in October 1998; he applied patches in addition to contributing dissectors to the program as well. More experts continued to contribute to the project; all inspired by a certain protocol they wanted but could not be handled by the program. So they would copy an already existing dissector and contribute a code back.
In May 2006, the original creator (Gerald Combs) could not continue to use the trademark of Ethereal because he was changing jobs to CACE Technologies from his then employer Network Integration Services who were the owners of Ethereal https://en.wikipedia.org/wiki/Trademark trademark. As a result, the name of the program was changed from Ethereal https://en.wikipedia.org/wiki/Trademark to Wireshark. Development work continued on the program and in 2008 version 1.0 came out with most of the features implemented. This release of version 1.0 coincided with SharkFest, the first Wireshark conference officially known as the “Wireshark Developer and User Conference”.
Wireshark Competitors and their users https://en.wikipedia.org/wiki/Trademark
Some of the competitors of Wireshark include Microsoft Network Monitor 3, IP sniffer and CommView 5.5 build 544 among many others. The Microsoft Network monitor 3 is normally used by network administrators to examine the traffic and it can capture data files from multiple cards of a LAN. The IP sniffer specializes in packet filtering, decoding and selection of network filters among other advanced functions like monitoring of IP addresses.
CommView 5.5 build 544 is suitable in environments that require the LAN as well as internet packets to be monitored. It also contains excellent multilingual support features. Despite the outstanding features of these competitors and the many others available in the market; Wireshark remains the leading network protocol analyzer and the most popular in the world.
What’s needed to install Wireshark
First, you need to identify reliable distributors of Wireshark for different platforms like windows, Linux and Unix; depending on which platform you are using. A special driver called WinPcap is needed; this is the device that is used to have the packets captured from the network. To install Wireshark and have it ready for use, you must obtain the binary package for the operating system that you are using plus the source after which you can now build the program (Wireshark) for the operating system.
The best place to download from is https://www.wireshark.org/download.html. Once here you will always see a list of the necessary files for downloading like wireshark-setup-0.99.4.exe and WinPcap_3_0.exe, there could be new files from time to time so it’s advisable to download the new ones. After downloading the necessary files, run the Wireshark setup file until it completes followed by the WinPcap setup file. After installing successfully, Wireshark can now be used to perform its functions like viewing Ethernet packets.
What does it find?
Wireshark simply finds the real-time network traffic which it decodes to give out meaningful data to be used by the network administrator in diagnosing any network problems that can hinder performance. Wireshark can also find and pull out plain passwords from a network. Specifically, Wireshark can find out a collection of important information including the following:
- Service denial attacks
- Network traffic logs that can be used for forensic analysis
- Network intrusion details
- Network bottlenecks and issues
Perhaps from what can be considered a negative view, people with wrong intentions can use Wireshark for all the wrong reasons like getting usernames plus passwords, locating very sensitive personal information, OS fingerprinting and network mapping.
Protocols supported by Wireshark
There are about 700 protocols that are supported by Wireshark and since it is an open source program, new dissectors continue to be created consistently as users need them to serve different purposes. Dissectors are the drivers that Wireshark uses to decode and translate different protocols.