Asked By
johnny
120 points
N/A
Posted on - 04/20/2011

Nowadays, wireless LAN is widely used, as it is very convenient for building a network easily, without managing physical cables.
So please, I want information as to what unauthorized actions might be committed easily, in a wireless LAN environment.
Thanks.
Answered By
ballileo
0 points
N/A
#86030
WLAN Security Threats caused by unauthorized actions

Dear Johnny,
The following unauthorized actions may be committed easily in a wireless LAN environment where proper security measures have not been taken:
1. Unauthorized use of network
-
Posing as another person by using the other person's IP address.
-
Various attacks via the internet.
-
Creating a stepping stone for unauthorized access (sending spam mail).
-
Consuming bandwidth, causing slow access speed.
2. Tapping Communication
-
Leakage of a user ID and password.
-
Leakage of confidential and personal information.
3. Unauthorized access to information resources
-
Information theft, alteration and deletion caused by file sharing.
-
Mounting an improper program such as a virus.
Answered By
TERRY U
5 points
N/A
#86032
WLAN Security Threats caused by unauthorized actions

Wireless local area network (WLAN) is nowadays the main connectivity option in many sectors due to many reasons, such as ease of installation, flexibility, mobility, reduced cost-of-ownership, and scalability. However, regardless of the benefits mentioned above, WLAN have some security threats which are discussed below. Basic components of a WLAN are access points (APs) and Network Interface Cards (NICs)/client adapters.
Wireless client adapters connect a PC or workstation to a wireless network either in ad hoc peer-to-peer mode or in infrastructure mode with APs (will be discussed in the following section). Available in a PCMCIA (Personal Computer Memory Card International Association) card and PCI (Peripheral Component Interconnect), it connects desktop and mobile computing devices wirelessly to all network resources.
The NIC scans the available frequency spectrum of connectivity and associates it to an access point or another wireless client. It is coupled to the PC/workstation operating system using a software driver. The NIC enables new PCs to be connected instantly to the network and enable Internet access.
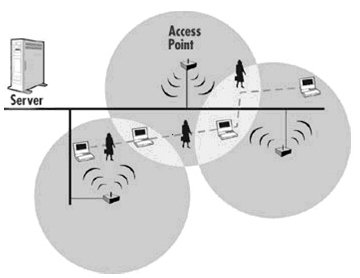
The WLAN components mentioned above are connected in certain configurations. There are three main types of WLAN architecture: Independent, Infrastructure, and microcells and roaming.
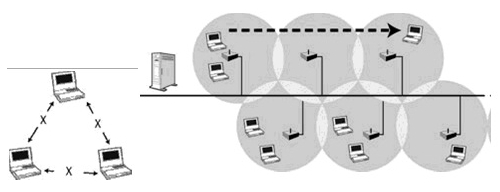
(Independent)
(Infrastructure)
(Microcells and Roaming)
We will NOT go in details of these BUT have pointed out the options available. The Unauthorized actions which can be performed on the WLAN without proper security are:
Denial of Service-
In this kind of attack, the intruder floods the network with either valid or invalid messages affecting the availability of the network resources.
Spoofing and Session Hijacking.
This is where the attacker could gain access to privileged data and resources in the network by assuming the identity of a valid user.
Eavesdropping.
This involves attack against the confidentiality of the data that is being transmitted across the network.
In order to secure your WLAN there are multiple tools which can be used. Try to go through this site. Which will explain major security options to secure the WLAN.















