Archive
Inventory Management Software for IT companies for hardware asset management
Inventory management application or software is one of the computer based method for tracking creation levels, orders, deals as well as deliveries. It may also be utilized in developing industry to make a work instruction, bill of substances as well as other production linked texts.
Companies utilize inventory management application or software for avoiding manufactured goods overstock as well as for hardware asset management. Inventory management application or software is one kind of tool to organize inventory information which before was usually gathered...
Read moreCloud Computing Rates
One of the latest technological advances that have managed to reap a lot of rewards is cloud computing. Basically, cloud computing is computing that is totally based on the internet.

This means that all resources that are shared, such as software, information and every other important requirement are provided to computers specifically on demand. Basically, the evolution of widespread adoption of architecture that is service oriented, virtualization and utility computing has resulted in the advent of cloud computing. Simply put, cloud computing provides users with...
Read moreLatest Security Updates in different OS
Latest Security Enhancements in windows Vista
Following are few of the latest updates, which has been carried out in the current type of windows Vista:
1. Windows Vista has recently more confined its sandbox for marked applets.
2. A client can now have pretty less privilege as compared to if he was availing another Windows operating system.
3. For demonstration, on another operating system than Windows Vista, a client is provoked with a protection alert dialog-box, which he should respond while running a marked applet. If you click ‘Yes’, the applet will enjoy whole authorizations to sprint...
Read moreLeading operating systems
Windows 3.0 & 3.1
Microsoft entered the operating systems market with the Windows 3.0 (released in 1990) and much improved version Windows 3.1 (released in 1992). Windows 3.1 was improved and had the capability to multitask with the DOS.

However, the memory sharing issues were not resolved. Both the DOS and Windows successfully ran in the same segment of memory.
Windows 95
Windows 95 was a major step forward from older versions i.e. 3.0 and 3.1. Windows 95 was released on the 24th of august 1995. For the first...
Read moreBest 5 Free Network Analysis Tool
Network analyzer is a tool used to analyze the properties of electrical circuits, especially those which are connected with the reflection and transmission of electrical signals known as scattering parameters. A Network Analysis Tool basically diagnoses specific problems that occurred in the computer hardware network and helps to explore it thoroughly. There are three types of network analyzers:
- Port Scanners
- Packet Analyzers
- Hardware Scanners
A Packet Analyzer is required to display and capture messages in particular that are processed by the network card of your computer. Hardware scanners supervise the network in order to detect malfunctions or...
Read moreDOMAIN NAME MANAGEMENT
World Wide Web (WWW) simply called web, is a way to access information over the internet. It is information for sharing or transferring model over the internet. The Hyper Text Transfer Protocol (HTTP) is used to transfer information.

Web services using HTTP's as a means for communication uses the web to share information. The Web browsers are used to access web documents which are known as websites. The websites contain information in the form of texts, graphics and multimedia's (audio and video).
A domain name is an identity, more specifically...
Read moreThe Top 5 Free Memory Optimizer
Memory optimizers are programs that analyze current RAM memory usage and check if these data are still needed by the current running programs. It’s primarily functions are to optimize memory and to detect memory leaks that could be possibly recovered. The memory leaks occur when too much memory is used but fail to return to operating system. As the leak builds up, the PC starts to slow down and can lead to a system crash if left unresolved.
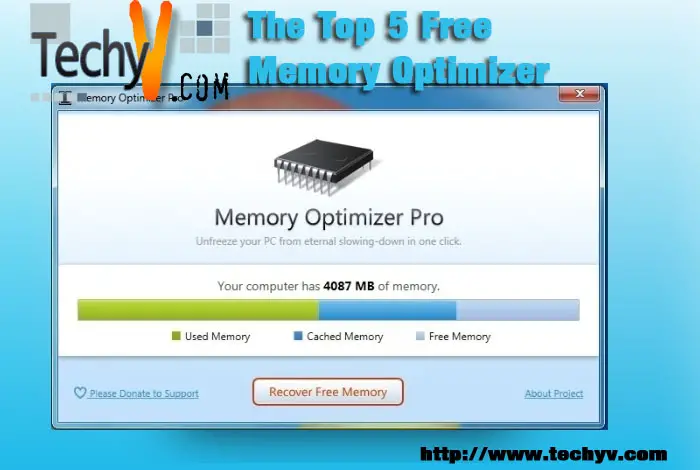
The cause of...
Read moreAbout PDA - Basic Info On PDA
The instrument that we know now as a PDA started out as a PalmPilot or a Microsoft Handheld Personal Computer machine. The difference in the two devices is that the Palm uses the Palm Operating System and the Microsoft uses its Windows Mobile operating system. If you buy a Palm PDA, it will probably have the palmOne either Zire or Tungsten manufacturer.

When Palm bought Handspring, Inc. Sony in 2003, it made the company known as palmOne. Palm PDAs are very popular because they have a over 20,000...
Read moreApproaching Web 2.0 and all its issues
All about Web 2.0
The notion of Web 2.0 started with a seminar brainstorming meeting between O'Reilly and MediaLive International. Dale Dougherty, web pioneer and O'Reilly VP, documented that far from having crashed, the web was more significant than ever, with stimulating new submissions and sites popping up with astonishing regularity. What's more, the businesses that had endured to have some things in common. Could it be that the dot-com disintegrate assessed some kind of rotating issue for the world.

a. The Web as...
Read moreConfiguring Hyper-V in Windows 2008
It will be helpful to begin by understanding a few important terms as follows:
Virtual means not real and refers to something that is just conceptual with no physical reality whatsoever, this term finds popular use among computer experts/scientists. It can be compared to an engineer’s design of a road; the design is not the actual road but is rather an imaginary road. A computer scientist can refer to the road design as a virtual road.
Virtualization: When used in computing, virtualization refers to the creation of a virtual version of some devices or computing resources...
Read more









