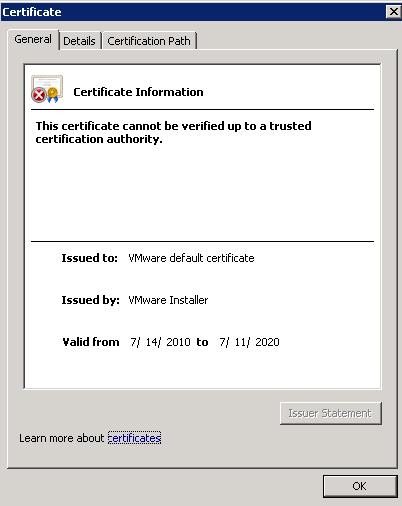
CA Problem with vCenter SSL Certificate

Hello friends
I recently tried to replace the default SSL on a vCenter 5 u1 server. I tried to do it but I could not succeed. One of my friends got an SSL certificate using IIS7. After this we both processed CSR using Thawte where we bought a domain validation SSL SS123 cert.
We used open SSL to get the rui.key and rui.crt and copied them with the rui.pfx to all the necessary locations on the vCenter server. By doing so we exported the SSL with the private key into the pfx format. I successfully followed all the steps I found on the website
I also took some help from other websites such as WoodITwork.com.
I completed all the steps successfully and after doing so I browsed the vCenter http url com but I got a certificate warning.
The screenshot of the warning is attached below:
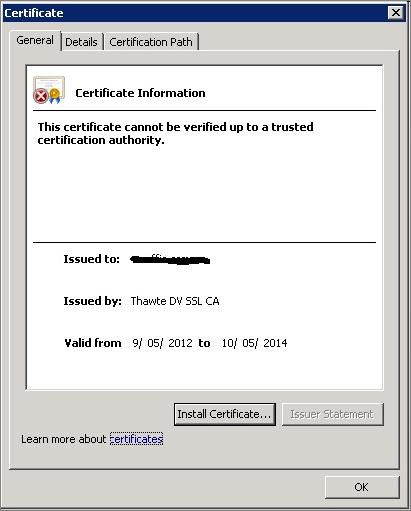
I checked it from the browser and found that SSL has already been installed but still I got the above warning. The warning reads:
“This certificate cannot be verified up to a trusted certification authority”
I then logged in to vCenter via the vSphere client but I got another warning. The screen shot of the warning message is as follows:
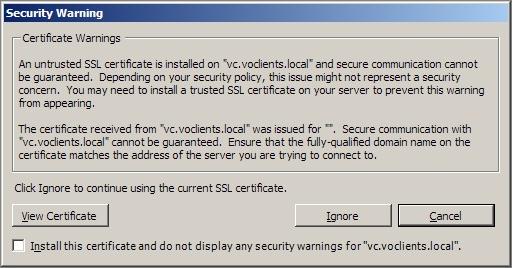
Security Warning
Certificate Warnings
An untrusted SSL certificate is installed on ‘vc.voclients.local' and secure communication cannot be guaranteed. Depending on your security policy, this issue might not represent a security concern. You may need to install a trusted SSL certificate on your server to prevent this warning from appearing.
The certificate received from vc.voclients.local was issued for . Secure communication with ‘vc.voclients.local' cannot be guaranteed. Ensure that the fully-qualified domain name on the certificate matches the address of the server you are frying to conned to.
Click Ignore to continue using the current SSL certificate.
View Certificate Ignore Cancel
Install this certificate and do not display any security warnings for ‘vc.voclients.local”.
Then I checked the Thawte SSL checker online to know the status which gave me the following error message on my screen:
“The intermediate CA certificates cannot be found for the following certificate chain.”
I have encountered another problem also which I don’t know if anyone else has also experienced before. The documentation asks to use the password on the pfx file of "testpassword". Now the problem is that if any one of them is authorized to gain access to a vCenter server, they will easily steal the pfx if they know the password.
What can be done to fix this problem?
Let me tell you that I few years ago I successfully made SSL work on vCenter 2.5 with the same method. I wish VMware provides a tool to perform such SSL tasks as it has become very difficult now with having to change 3 or 4 different places.
Your suggestions are required to fix the issue.
Waiting for your concern