Recent posts
The application we are developing requires to find the levels of authority for a given user. The levels of authority follows a hierarchical tree like structure. An employee can have any number of supervisors. In order to traverse the tree structure, it is proposed to use recursion or a...
Read more
Installation and Configuration of Network Card in Windows 7 In this article, we will install a network card in Windows 7 and configure the network card. If you want to add your computer to a network or any network device, you need to install or configure the network card....
Read more
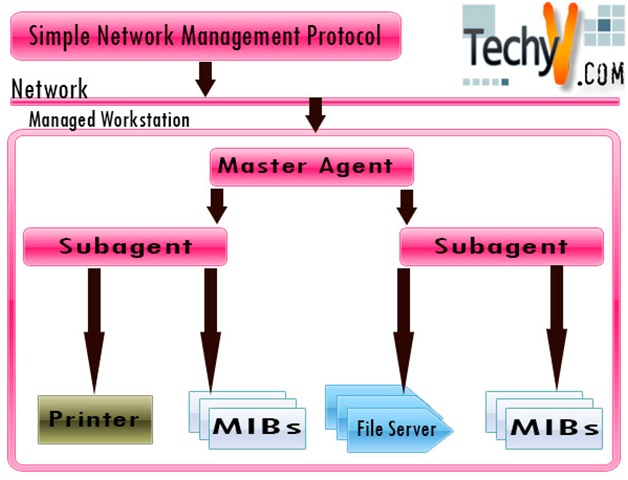
SNMP: Simple Network Management Protocol Introduction What does Network Management mean? If you have a network of computers, hardware devices like switches, routers, database servers and workstations, surely you will have to: Keep track of the settings of each device and its functioning. Check whether the network is running smoothly and...
Read more
How many table views are available in Ms Access? And is it possible to switch between them or not? Help me understand the concept.
Read more
I want to clear my concepts about the semantic object views in databases. Can anyone guide me in detail? I am waiting for the experts to respond.
Read more
We have a requirement to use JBoss as the application server for a web application. The web application is fully tested and ready. We have a Linux box as the production server. We require to run the web application on the production box under Jboss. Our development environment was...
Read more

Microsoft Publisher Definition: As the name suggests and hints about the application from the marketing world. MS Publishers a DTP application from Microsoft created which proves to be a big challenge and an option for some of the applications like Adobe and QuarkXPress. This application has originated...
Read more
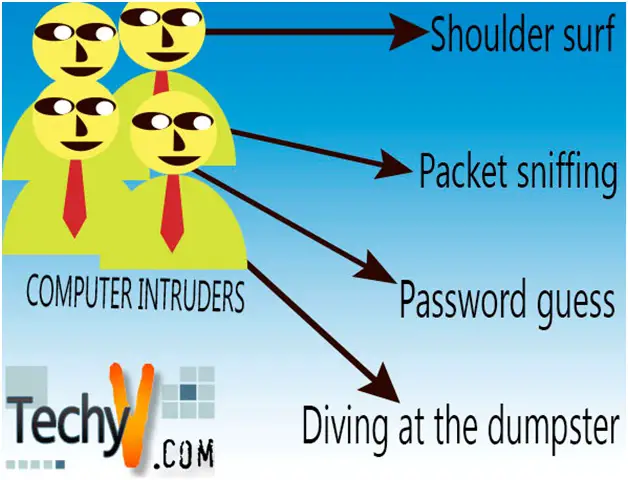
COMPUTER INTRUDERS Computers are among the most sophisticated machines around the globe; moreover, they carry very important and vital information. This vital information needs to be secured from both external and internal attacks. Many people go extra mile to secure their computers using different techniques and methods including passwords,...
Read more

Rich Internet Application explained in detail It is an Internet application that contains a number of features from normal desktop applications and is usually abbreviated as RIA. White paper introduced Rich Internet Application in the year 2002 by Macromedia which later advanced to become Adobe. However this principle was...
Read more
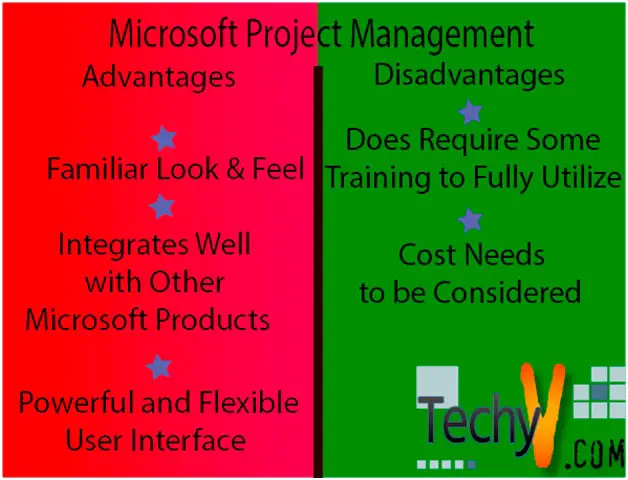
Microsoft Project Management The process of project management is a very crucial one for many organizations and individuals. Project management involves the planning, organizing, directing and controlling an organization’s or individual resources for a specified time in order to accomplish a specific short term objective established to complete goals...
Read more











