Recent posts

Everything You Need to Know About Domain Space TCP/IP uses an IP address to uniquely identify the host to the internet, however remembering the IP address all the time is difficult. So instead of using an address, it uses names and thus, the DNS provides this mapping address to...
Read more
Top 5 File Transfer Protocol (FTP) Software In the recent years there has been a continuous increase in the number of people who have personal or business websites and WordPress blogs. With this increase, the demand for FTP client programs which can upload or download the data to and...
Read more

Top 5 Screen Capture software Screen Capturing Software applications are extremely useful resources for all web developers and designers. Such programs are useful in capturing an image or images of certain visible screens from your computer monitor whether it is the web or desktop. Screen capturing applications provides these...
Read more
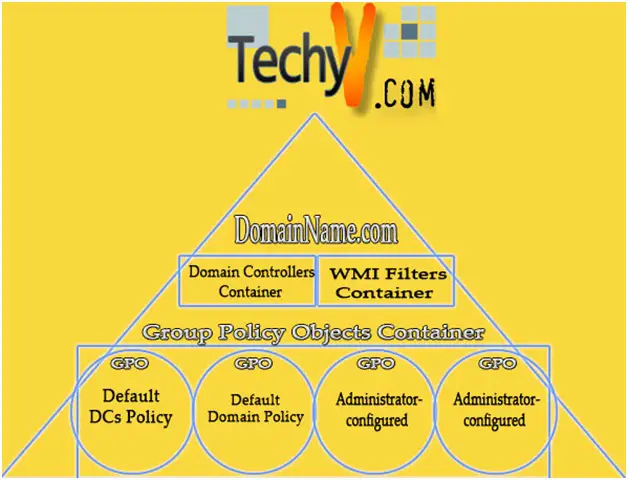
Managing Group Policies with Command Line Tools When it comes to the utilization of Group Policy in MS Windows XP, it means to characterize client and PC settings for the assemblies of clients and PCs. In this process, we conceive an exact desktop setting for a specific assembly of...
Read more

What is WiFi? WiFi is simply defined as a wireless networking technology; a way of connecting computer devices without cables. With the WiFi technology, you can access broadband internet without using any cables, be able to get to your email and other online resources from any location in your...
Read more
Top 5 Free Vector Graphics Tool A vector is defined by two major properties; magnitude and direction. The term also depicts the mathematical or geometrical representation of entities like velocity, momentum, force, electromagnetic fields etc. Vectors are portrayed graphically in two or three dimensions. Graphic is the creative way...
Read more

Top Five Free Secure Erase Utilities A Secure Erase Utility is an application that overwrites data in order to completely destroy the electronic data residing on a digital media or a hard disk drive. Sensitive data such as bank account details, credit card numbers or medical history are often...
Read more
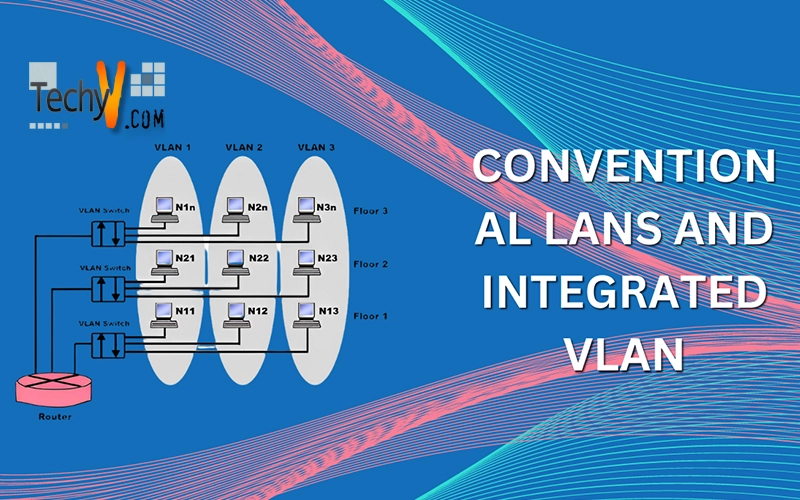
Conventional LANs and Integrated VLAN LAN (Local area network) is a network that is up to an office or building multiple numbers of computers is used that are connected through switches. LAN is a medium and small size business. LAN has feature that it can be handled easily because...
Read more

Comparison between Universal, Global and Local Security and Distribution Groups The following are two types of assemblies to choose from when contriving a new assembly in Microsoft Active Directory: Security Such assemblies permit you to organize client and PC to get access to distributed resources. We can...
Read more

Service Oriented Architecture Service Oriented Architecture is a technique used in software development based on the concept of Service. A service can be defined as an independent function which is well defined and self contained. In SOA, different services communicate with each other to perform some activity. Even two...
Read more











