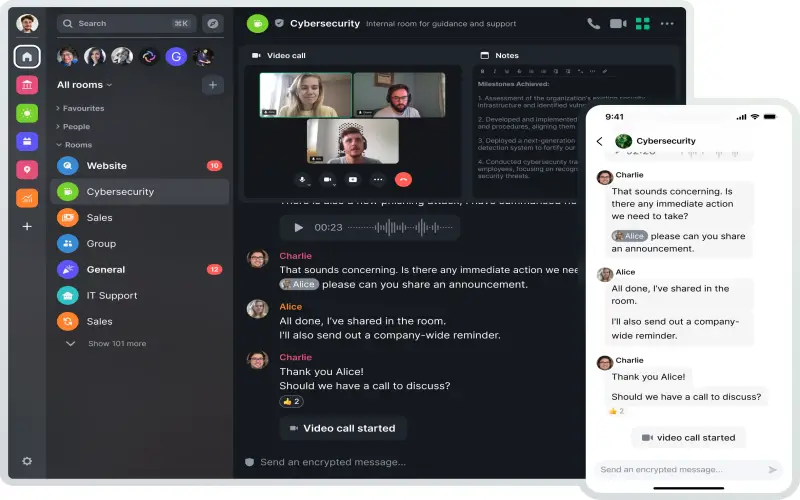
Encrypted chatting is vital in this Digi-first world, no cap. Folks need that secure SMS to confide their inner thoughts and block the feds from snooping. But nailing down the best end-to-end privacy app requires watching their encryption schemes, audits, whether source code drops publicly and if the biz seems trustworthy or just money-hungry, you get me? I’m breaking down the top 10 most lock-tight encrypted messaging setups for 2023 from my personal experience. Big ups to apps with encryption certifiably blessed by crypto experts defy no exploits or fraudulent claims on the CV. Major Bonus points if everything checks out fully transparent, not closed source shady. Is the app maker focused steadily on user privacy or are they just in it for the paper? My rankings factor in whether an app hits the mainstream with everyday folks plus headlines in privacy news rags among activists and whistle-blowers. An app can have fly encryption but if barely anyone using it then the impact is kind of low. I also peep if they encrypt metadata like who you talk to and when.
1. Signal
Topping most privacy lists, Signal is the gold standard for state secrets level encryption designed by some glowingly endorsed cryptographers. They stacked encrypted identities, session keys, signing keys, and more into a vogue cipher suite. Signal devs keep their infrastructure encrypted and closed off while publishing open-source clients for all to peek at. A non-profit, Moxie Marlinspike’s team ships app updates focused on privacy above all, not ads and stuff. With OG cred for public awareness of encrypted messaging, Signal lacks in user numbers but brings best-in-class security and small metadata collection to the table.

2. Telegram
Fast and fluid performance has made messaging mainstay Telegram a smash hit. But its custom in-house encryption whipping by founder Pavel Durov makes some folk twitchy. Secret Chats and calls have that end-to-end goodness powered by a funky combo of AES and RSA encryption plus Diffi-Hellman key magic, but audits keep surfacing security dings. Durov swears there’s no sneaking backdoors, although Telegram can view messages to block abusers. Open-source clients would let people peek at Telegram’s cipher suite but they keeping it closed for now. Major props for viral user counts yet their metadata collection for “transparency” seems sus.

3. WhatsApp
WhatsApp encrypts chats and calls by default via Signal Protocol blessings. Going through frequent security reviews to implement encryption properly, WhatsApp seems focused on keeping convos secured despite parent company Meta’s hunger for people’s deeds. Cryptographic signatures on messages check for tampering, although saying they limit metadata collection while permitting themselves to siphon data for marketing seems questionable. And news about them leaving an exploit open for government malware previously shakes trust. Convenient and encrypted yet thirsty for data, WhatsApp essentially Facebook in chat app form.

4. Threema
Users can forego linking phone numbers or email addresses to Threema IDs. Instead, users can securely verify identity keys in person. Deployed on over 10 million devices, Threema recently underwent an external code audit confirming solid encryption implementations aligning with industry best practices. Threema’s closed source code may deter some privacy advocates. However, Threema publishes security design outlines, offers a bug bounty program to incentivize responsible disclosure and penetration testing, and undergoes third-party evaluations.

5. Wire
Boasting over 100 security improvements and third-party penetration tests within the past year, encrypted messenger Wire continually refines protections for its 50 million users. Wire utilizes the Axolotl ratchet algorithm popularized by Signal to provide forward secrecy. Wire offers secure audio calls, video conferencing, and file sharing. Companies like AWS trust Wire for secure team communication. Unique features like visitor masks even obscure metadata like IP addresses to protect user identities.

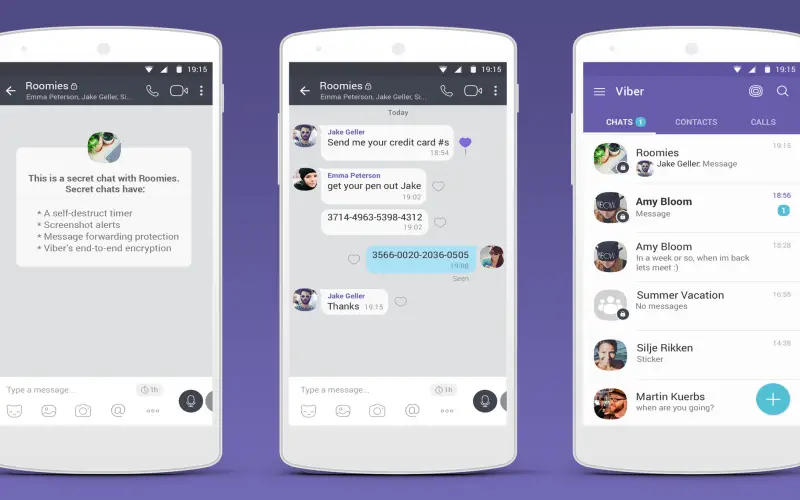
6. Viber
Offering default end-to-end encryption since 2016, Viber provides security features like disappearing messages and password-protected chats to over 1 billion users. Viber uses its encryption protocol rather than popular frameworks like Signal or MTProto. While details remain limited for security through obscurity, Viber underwent multiple internal and external penetration tests. Unique features like chat extensions offer encrypted connections to external apps as well. However, Viber shares certain usage analytics and technical data with parent company Rakuten per its privacy policy. Metadata risks exist despite message encryption protections. As Viber continues growing its worldwide user base, its encryption scheme merits ongoing scrutiny to ensure it evolves accordingly against emerging attack vectors.
7. Snapchat
Known for ephemeral messaging, Snapchat deploys end-to-end and transport layer encryption to protect over 300 million users. By default, messages auto-delete after viewing. Users also control if recipients screenshot messages. However, experts argue weaknesses like the reuse of encryption keys with predictable nonce values undermine protections. Without open-source code or completed third-party audits, questions persist about whether Snapchat’s ad hoc encryption schemes properly defend against spoofing, decryption, and metadata analysis over time as computational power increases.
8. CoverMe
Boasting over 100 million downloads between iOS and Android devices, encrypted messenger CoverMe offers forward secrecy and key verification via QR codes. Users can also password-encrypt offline messages. CoverMe underwent internal and external penetration testing, providing alerts on potential vulnerabilities. Continuous security updates resolved issues accordingly. CoverMe also operates a bug bounty program with an encryption-focused scope. However, CoverMe’s closed source code and China-based development team sparked some user distrust regarding backdoors.
9. Ricochet
Security researchers built the experimental messenger Ricochet specifically for metadata protection. Ricochet routes messages via Tor onion services to hide users’ real identities. The app minimized data collection to thwart surveillance. Ricochet’s small user base allows only basic testing for cryptography vulnerabilities. However, its premise disrupts traditional metadata collection, the key to anonymity. Some groups may view Ricochet’s limitations on contacts and messaging as warranted trade-offs. While adoption remains niche, Ricochet’s metadata focus warrants monitoring as an anit-surveillance experiment.
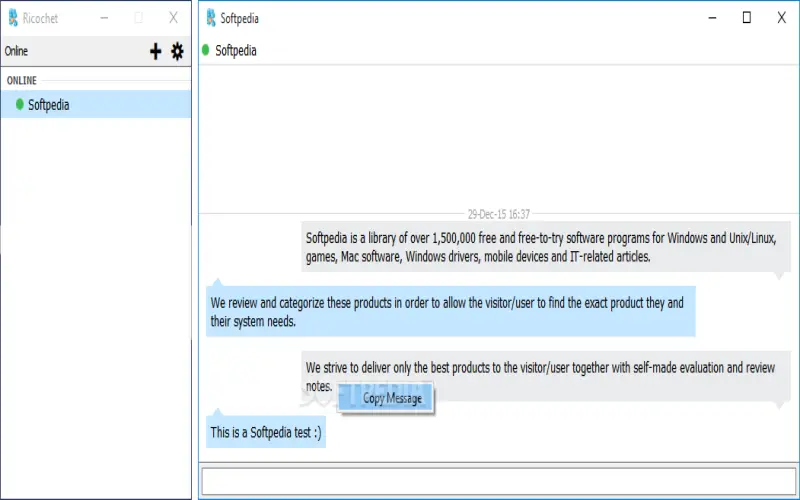
10. Element.io
Offering end-to-end encryption for messages and VoIP calls, open-source messenger Element acts as a client for the Matrix protocol decentralizing communication. Element builds encryption on the Olm and Megolm cryptographic ratchets popular in other apps like Signal. Element underwent several external audits confirming proper encryption implementations matched designs. Unique social features like public rooms and communities allow usage at scale while preserving individual user ownership of data.