
When we talk about the Information Systems Security, we use cipher algorithms to Encrypt or Decrypt data.
What is the basic work of the cipher and the basic concepts use in these ciphers.
-
Caesar Cipher
-
The Perfect Substitution
-
The Vernam Cipher
-
Block Cipher
-
Stream Cipher
Answered By
alphae
15 points
N/A
#84363
The basic work of the cipher

First of all we have to know that a cipher is a concealed way of writing messages so to protect them from access by unauthorized persons.
The Caesar Cipher – in this cipher, every plain text letter is substituted with another letter that is an unchanging number spots down the alphabet.
In the example above, the cipher for B will be C, C will be D and D will be E.
Perfect substitution cipher – plaintext is replaced by ciphertext following a given defined system. A string of random bits which are of the same length as the plaintext are chosen, they are then used to find the corresponding ciphertext using XOR.
e.g. p1 p2….. pn -plaintext
b1 b2……bn
c1 c2……cn -ciphertext
The vernam cipher also referred to as the one time pad, it uses a character to character combination of plaintext to produce ciphertext. To convert the ciphertext to plaintext, one would use a character to character combination of the ciphertext to produce the plaintext.
SENDING
message: 0 0 1 0 1 1
pad: 1 0 0 1 1 0
XOR ——————
cipher: 1 0 1 1 0 0 1
RECEIVING
cipher: 1 0 1 1 0 0 1
pad: 1 0 0 1 1 0 0
XOR ——————-
message: 0 1 1 0 0 1 1
A block cipher is whereby a cryptographic key operates on a group of bits as opposed to a single bit only. The block size may be 64 bits, 128 bits or sometimes variable in size.
In a stream cipher, there is change on individual plaintext digits as the time changes. Unlike the block cipher, the plaintext is encrypted one bit at a time in the stream cipher, hence the encryption of each digit is completely reliant on the current state.
The basic work of the cipher

When we talk about modern computer networking, ‘cipher’ has got extreme Importance. So before we start in detail, let me tell you the basic concept of cipher. The method of masked communication is known as cipher. The information is send through codes to conceal the original message.
Caesar cipher: The code breaker program which assists you to read the original message. The program allows you to encipher and decipher the code. Online support is also available for this purpose. I am including a link for that.
The Perfect Substitution Cipher: It leads the user to convert simple, original message to perfect secrecy level. The information is in the form of random bits. The algorithm choose the random bit and XOR them to provide security.
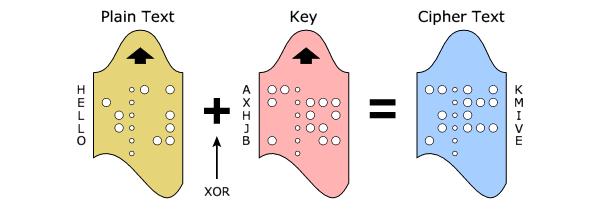
Vernam Cipher: The method is almost same in this cipher. We have a plain text and a pre-recorded Key. The bits of original message are XOR with the KEY, and it becomes the cipher text which can be transmitted easily. At the receiving side same strategy is used to get the original message. The figure gives detail description.
Block Cipher: The original message is broken in the form of fixed length blocks which are further encrypted to secure the message. The importance of block cipher is in the bulk data. It deals with the 2 paired algorithms each having 2 inputs. 2nd input handles the secret key.
Stream Ciphers: It is a symmetric cipher having time varying transformation on every bit of the original message. It differs from block cipher because the previous one has fixed transformation. The basics involve the Running-key or key-stream, a sequence of bits, combined with the bits of original message to provide secrecy.













