Recent posts
Checkpoint Firewall – the best at all times There are a number of security software around that claim to be more effective when it comes to the protection of networks and overall business processes. Most of them come along with different hardware, which make the processes of protection more...
Read more
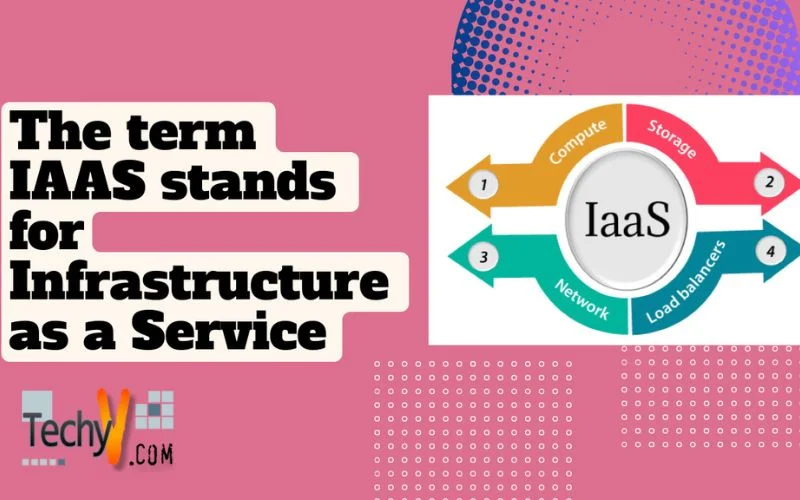
CLOUD COMPUTING - IAAS The term IAAS stands for a company acronym Infrastructure as a Service. The service is provided to the consumers to store, process, and facilitate the fundamental computing resources. In this service, the keeper can rely upon for taking chances including operation systems and applications as...
Read more

Back up: History, Types and Devices In our everyday life, a lot of things come and go, but we need something we can go back to for us to continue and base our decisions from. That is where the word back-up comes in. Back-up is an idiomatic expression that...
Read more
Avira Antivirus Avira Antivirus is among the most popular when it comes to efficiency in protecting your computer. Its popularity is related to the thoroughness and holism of its scanning capabilities. This can be quickly installed to your computer and is highly...
Read more

Delegation in exchange 2007 & 2010 Delegation in exchange 2007: It is necessary to know how to delegate server-administration-2007. Microsoft-Exchange-Server 2007 gives the capability for the Exchange-administrators to delegate executive as well as management blame for the server to the individual otherwise assemblage of personal when it works in a...
Read more

HP Client Automation The Right Software Solution for Your Business Needs HP Client Automation is an automated tool that is used to manage routine computing tasks. This software seeks to reduce the amount of time users have to spend on basic computing tasks,...
Read more

BitLocker and its standard criteria Bitlocker and its criteria BitLocker is a disk encryption software. Its function is to secure data by providing encryption for the entire drive. BitLocker is featured only in the latest versions of Microsoft OS such as Windows vista, Windows 7, Windows server 2008, and...
Read more

Microsoft Outlook rules explained Microsoft Outlook manages personal information of a person. It is available as a separate application as well as included in Microsoft Office. It is an application which helps a person manages his email. Apart from providing email management, outlook also offers a task manager, calendar,...
Read more
Unified Messaging The new Unified Messaging (UM) server role in Exchange Server 2007 extends the functionality of your Exchange messaging infrastructure, allowing it to transmit and store more than just traditional e-mail. As more established communication solutions (Voice and fax) find a new life on IP networks, a new means...
Read more

User Access Control With the increasing use of computer and information technology in all aspects of life, the importance of information security has increased concurrently. Microsoft has successfully dominated the market. Its Operating Systems have become the most widely used system application all across the globe. Microsoft Operating Systems have...
Read more











