A subfield of quantum information science called quantum cryptography makes use of the laws of quantum mechanics to create secure communication channels. It uses uncrackable encryption keys made possible by quantum phenomena like superposition and entanglement, and it can also spot any unauthorized eavesdropping. Numerous developments in quantum cryptography have taken place throughout time, opening the door for ground-breaking improvements. To protect and transmit data in a way that cannot be intercepted, quantum cryptography employs the inherent features of quantum physics. Data is encrypted and protected using cryptography so that only those with the proper secret key may decrypt it. In this article, we have the Top 10 Revolutionary Breakthroughs In Quantum Cryptography.
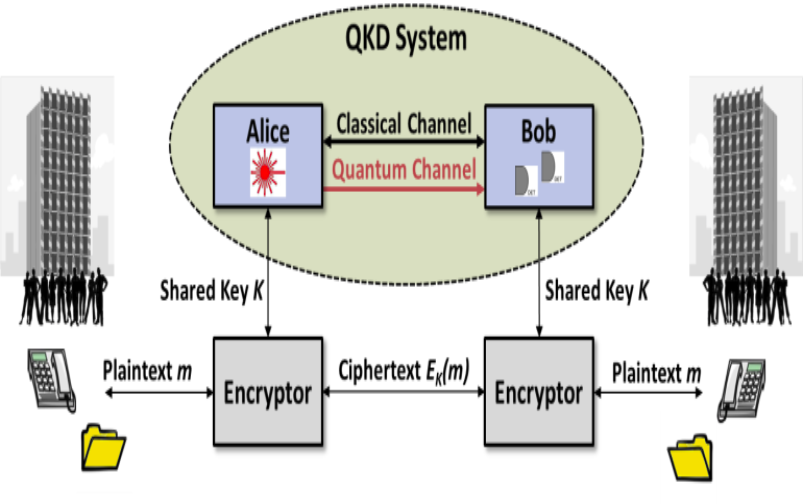
1. Quantum Key Distribution (QKD)
The core concept behind quantum cryptography is quantum key distribution. It enables two people to safely create a secret key even when there is an eavesdropper present. Quantum key distribution (QKD) generates encryption keys that are impenetrable to eavesdropping and offers communication channels unparalleled levels of security.
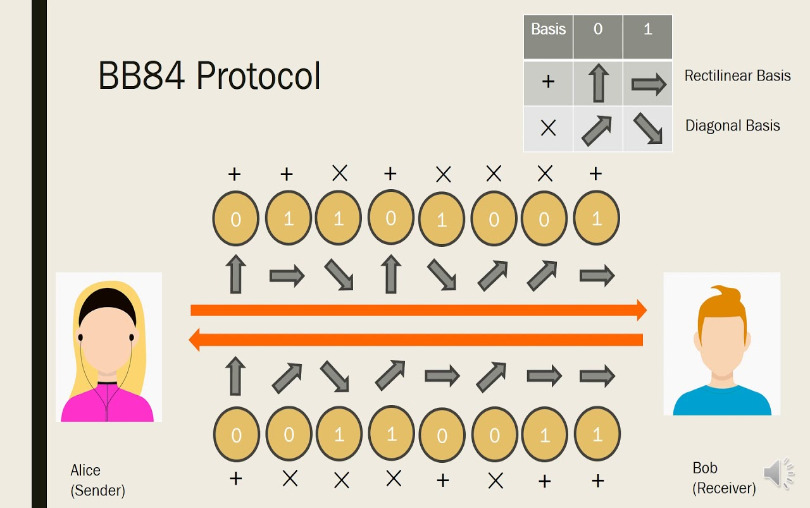
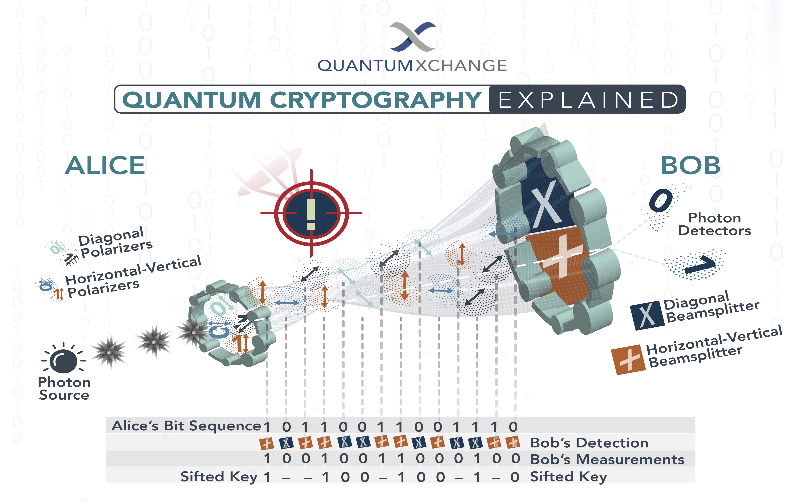
2. BB84 Protocol
One of the first and most well-known quantum key distribution systems is the BB84 protocol, created by Charles Bennett and Gilles Brassard in 1984. Information is encoded using quantum states, and the encryption key is safely sent between the communication parties via a set of impartial bases.
3. Quantum Cryptography Networks
Networks using quantum cryptography have been successfully demonstrated by researchers, allowing safe communication between several nodes. By dispersing encryption keys across several sites via these networks, safe quantum communication is made possible on a greater scale.
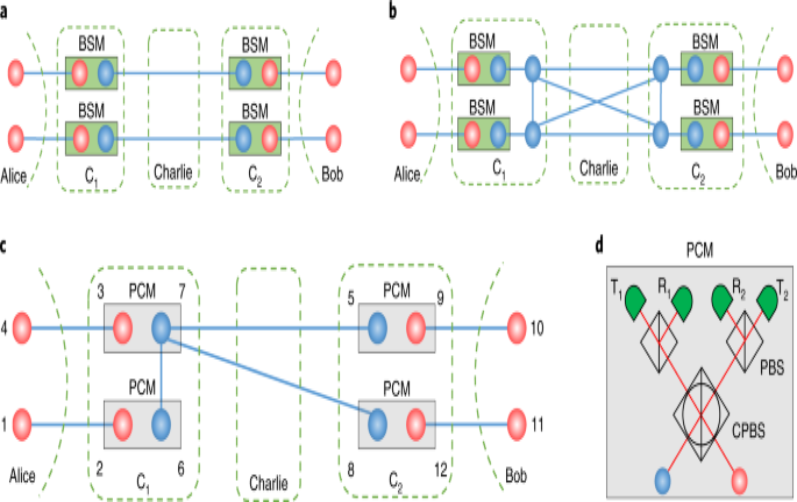
4. Quantum Repeater
Quantum communication over great distances requires quantum repeaters. By reducing the loss of quantum information, they enable the transmission of quantum states across long distances. Quantum repeater technological advancements have opened the door to secure quantum communication over very long distances.
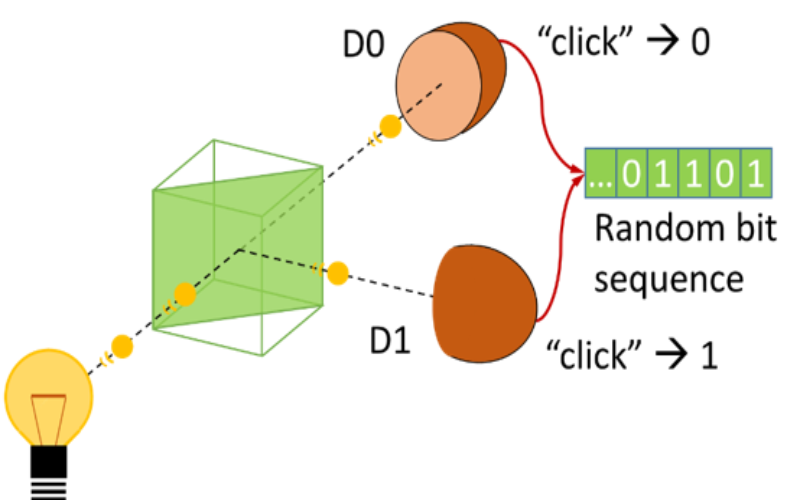
5. Quantum Random Number Generators (QRNG)
In encryption methods, random numbers are essential. To produce truly random numbers, which are essential for cryptographic applications, QRNGs use the intrinsic unpredictability of quantum mechanics. The development of QRNG technology has given quantum cryptography a safe source of randomness for key creation.
6. Device-Independent Quantum Cryptography
Device-independent quantum cryptography seeks to dispel faith in the quantum communication equipment itself. Even if the gadgets are tampered with or inadequately described, security is still ensured. This innovation enables the use of more reliable and secure quantum communication protocols.
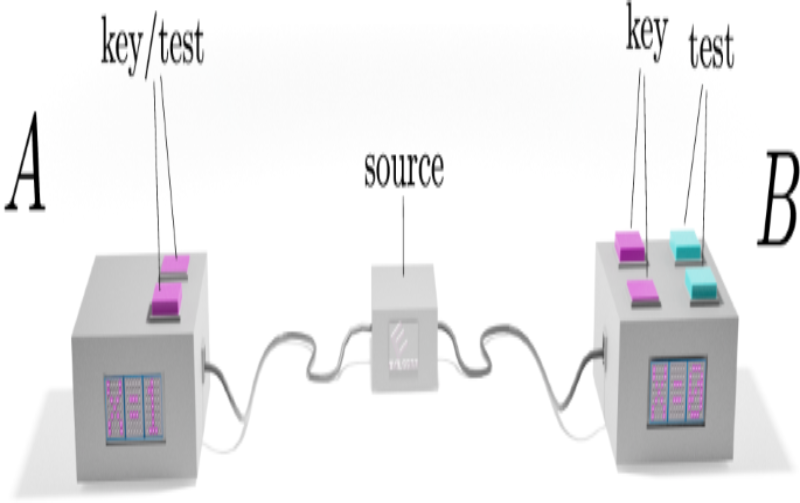
7. Measurement-Device-Independent Quantum Key Distribution (MDI-QKD)
A quantum key distribution that is independent of the measurement devices employed in the protocol is known as a “measurement-device-independent quantum key distribution” (MDI-QKD). To protect against side-channel attacks and device flaws, MDI-QKD employs untrusted measurement devices. This makes it a potential method for real-world quantum key distribution.
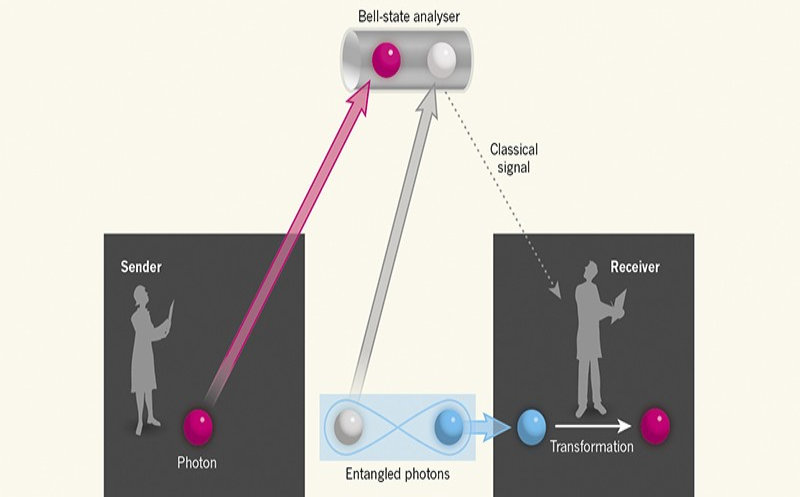
8. Quantum Teleportation
It is a phenomenon that enables the instantaneous transmission of quantum states from one location to another. The safe communication of quantum information between remote parties without the requirement for physical transmission is made possible by this development, which has important ramifications for quantum cryptography.
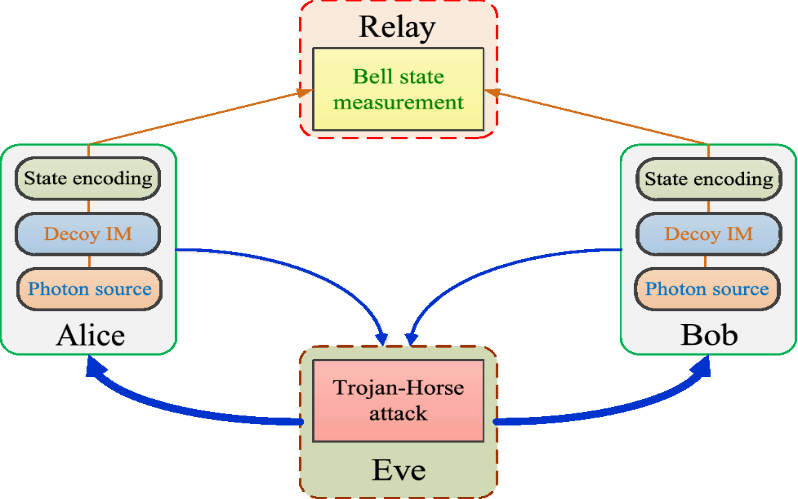
9. Techniques For Detecting Quantum Hacking
New methods have been developed by researchers to identify quantum hacking efforts. These methods entail keeping an eye on the transmitted quantum states’ properties and looking for any eavesdropper-induced changes. Quantum hacking detection approaches improve the security of quantum communication by spotting interference or abnormalities.
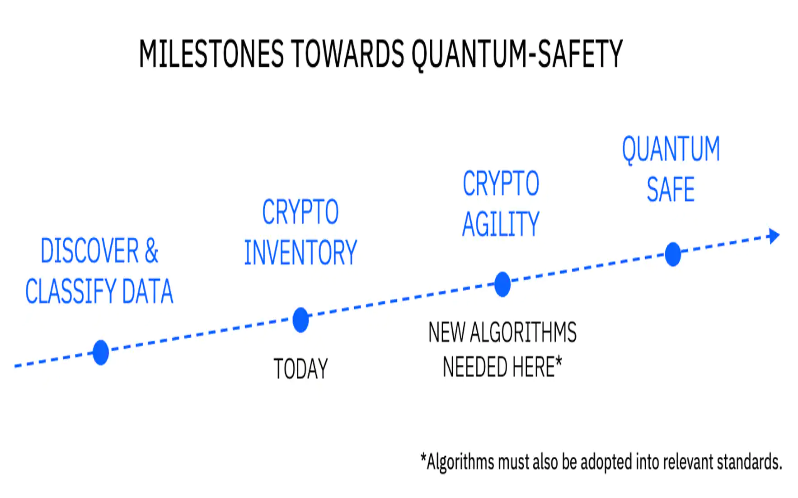
10. Quantum-Safe Cryptography
Because many conventional encryption techniques are vulnerable to quantum computing, current cryptographic systems are at risk. The process of creating post-quantum cryptographic techniques, commonly referred to as quantum-safe cryptography, entails creating encryption algorithms that are impervious to assaults from both conventional and quantum computers. In the age of quantum computers, long-term security is ensured through the creation of quantum-safe cryptographic techniques.