Data privacy and compliance mandates warrant resilient data masking schemes across test cycles. As part of regular reporting, DBAs need to evidence rigorous data masking to external auditors. I outline the top 10 leading data masking solutions that empower organizations to fully obfuscate sensitive data sets while preserving referential integrity. Effective data masking facilitates compliant analytics, testing, and development without risking exposure to confidential personal or financial information. However, subpar masking severely compromises data utility. The tools below enable granular policies to mask subsets of columns and rows while maintaining functional dependency between data elements. Both legacy and modern data formats require tailored approaches to parse file types correctly while scanning for sensitive data. Across industries, these fully-featured masking tools offer versatile options to configure roles, map data, substitute values, shuffle data, encrypt data, anonymize data and synthetically generate fake data. Implementing the optimal blend of masking techniques proves essential to balance privacy, quality, and usability based on use case specifics.
1. K2View Data Masking
K2View Fabric empowers rapid data delivery across complex landscapes. The integrated data masking module handles sensitive information across databases, files, and big data. As part of the fabric architecture, data masking integrates with data replication, validation, and monitoring. DBAs can mask column values using a library of over 20 predefined masking methods while configuring specialized domain-based masks. Extensive logging and dashboards detail masking coverage metrics per table and column.
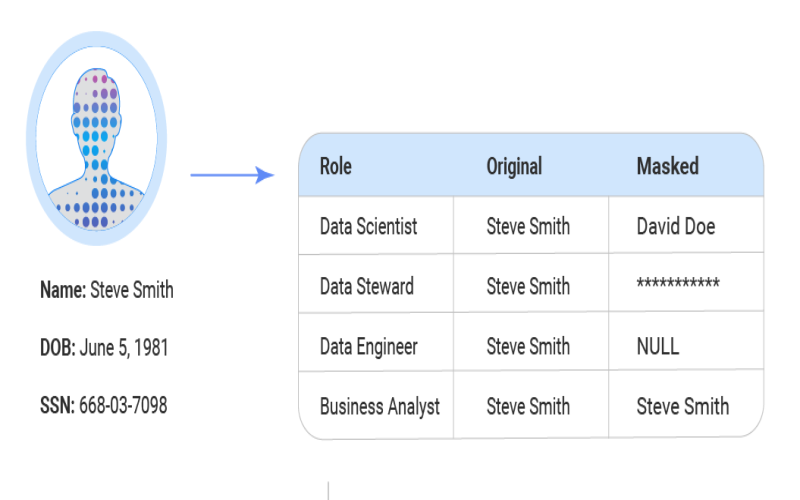
2. DATPROF – Test Data Simplified
DATPROF generates high-quality test data based on custom profiles without exposing original sensitive information. The Test Data Generator masks and scrambles source databases or flat files while maintaining referential integrity and functional dependency between columns. DBAs simply profile source schemas, select tables for subsetting, configure masking techniques per column, and execute test data generation batch jobs. Detailed logs quantify masked records and values. DATPROF removes the need to build test environments from copies of production.

3. IRI FieldShield
FieldShield handles high-volume data masking across diverse big-data infrastructure. As a scalable solution built for performance on distributed data, FieldShield integrates with popular repositories like Teradata, Oracle, SQL Server, DB2, Vertica, and Hadoop. DBAs can select dedicated masking approaches based on data types like numerics, dates, text, or images. Custom masking methods allow tailored logic like Luhn checks for financial data. Centralized field-level masking policies synchronize across environments while drill-down dashboards detail coverage.

4. Accutive Data Discovery & Masking
The Accutive platform automates the discovery and masking of sensitive data using scans tailored to country and region-specific privacy regulations. Accutive integrates with Snowflake architecture for large-scale data processing but also suits smaller data marts. The centralized dashboard maps detected sensitive information like credit card numbers while tracking scans. Data owners configure extensive libraries of redaction and substitution rules that propagate across sources. Detailed logs record masked fields and values at the column level. Accutive also enables direct data subject access request processing.

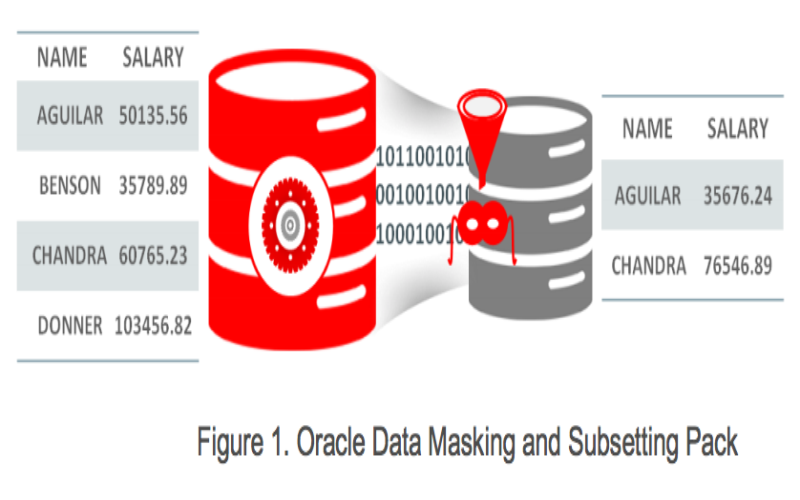
5. Oracle Data Masking And Subsetting
Part of the larger Oracle Data Safe suite, Data Masking handles sensitive information across Oracle databases (including Autonomous Databases) with format-preserving masking techniques. DBAs define data masking formats, substitution rules, and full masking policies before executing jobs. Integrations with Oracle Application Testing Suite then facilitate testing on masked datasets. Data subsetting and database vaults add row-level filtering while managing access. Custom masking formats allow unique business ID obfuscation along with monitoring overall coverage.
6. Delphix
The Delphix platform focuses on managing sensitive data to enable scalable DevOps delivery, testing, and reporting use cases. The integrated data masking engine discovers sensitive columns and masks using 25+ predefined techniques like shuffling, substitution, redaction, and encryption. Jobs propagate field-level masking policies across aligned sources and environments while retaining referential integrity. DBAs can further provision masked virtual copies of production data for developer sandboxes. Detailed logs throughout track environments, users, jobs status, and view masked values.

7. Informatica Persistent Data Masking
Informatica leverages its extensive data integration platform to persistently mask sensitive information across legacy systems including mainframes. The configuration console allows DBAs to scan sources, flag sensitive data, implement masking techniques per field, and execute jobs. Integrated workflows then incorporate the masked data sets into downstream testing or analytics while retaining key relationships. Informatica persistent masking suits highly regulated industries by further securing masked data itself and detailed audit trails.
8. Microsoft SQL Server Data Masking
Native to SQL Server, Data Masking limits exposure of sensitive information from test and non-production environments. DBAs select databases, tables, and columns to analyze and mask using predefined masking functions like randomizing financial data while retaining formats. Centralized masking rules propagate across sources. Integrations with SQL Server Profiler then track usage on masked data while Data Discovery and Classification discover and classify sensitive columns for governed masking.

9. IBM InfoSphere Optim Data Privacy
InfoSphere Optim offers a unified view across enterprise data sources to discover, classify, and mask sensitive information while monitoring usage. The data privacy dashboard maps detected sensitive data and coverage metrics across databases. Compliance policies and data subject access mappings drive granular masking routines tailored to over 100 jurisdiction regulations while retaining key relationships like unique identifiers. Domain value analyses guide optimal substitutions for distinct datasets. Dedicated workload replay assesses information loss.
10. BizDataX
The BizDataX sensitive data exchange platform focuses on securely sharing data with third parties to enable analytics use cases. Automated data inventory cataloging and classification feed into specialized masked data-building routines covering PII, financial information, healthcare data, and custom types. DBAs configure detailed data masks while regulating access. BizDataX further customizes masked views per the third party. Advanced analytic output testing validates the utility of shared masked data. Dedicated metrics demonstrate effective masking to customers.