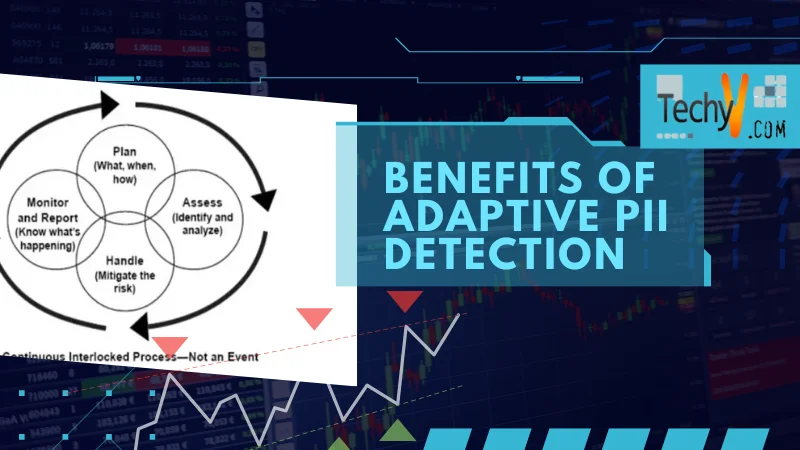
What Is Adaptive PII?
Adaptive PII is systems or strategies that strongly modify and develop their approaches to recognizing Personally Identifiable Information (PII) within datasets. These systems generally use machine learning or artificial intelligence algorithms to consistently learn from the latest data and adopt their detection methods accordingly.
Personally Identifiable Information (PII) is information that can rarely recognize an individual, such as a worker, a patient, or a user, “Sensitive PII” means as to data that, if endangered could pose a high risk to the individual’s secure and misuse of data for someone else’s gains. With various laws and rules governing the gathering, use, sharing, deletion, and protection controls of PII data and sensitive PII, management must visit complaints amongst the consistent passing of new laws.
Advanced users are well-informed about the essentials of their data, its potential misuse, and the results of its loss.
What Is PII Data Why Is It Important?
PII data term refers to the procedures of recognizing and selecting Personally Identifiable Information (PII) within a management data depository. PII is any data that can be pre-owned to identify a particular individual name, address, social security number, email address, phone number, financial data, and many more.
In the scheme of the marketing campaign, the sales group uses the primary data to change insights into paying users. In contrast, the business group uses the same data to process payments.
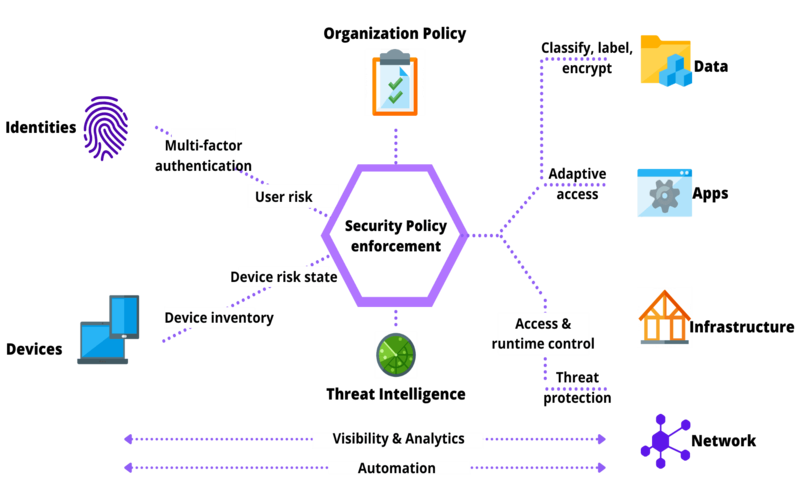
The Benefits Of Applying Adaptive Security
Adaptive security innovation offers a reliable reach to adjust and adapt to a business’s digital footprint.
- With Adaptive security, you can rapidly analyze, assess, and respond to protection vulnerabilities as they happen. You obtain the upper hand in beating potential breaches by consistently assessing incidents, users, systems, and network traffic. No more waiting in the dark; you can joyfully secure your business.
- Your attack exterior would be organized by forecasting and recognizing potential threats hiding in your company’s surroundings, such as software threats to unprotected employee endpoint tools and servers with risky open ports. Recognizing and minimizing these weak points will secure your military and generate an impassable fortress.
- With a complete actual-time view of your security attitude and evaluation of nature and incidents, you obtain a costly understanding, allowing you to take protective action before a breach happens. It means you can visit one step before malicious actors, secure your cost assets, and organize the trust of your contributors.
- Adaptive security allows your management to adopt and improve its protection attitude based on a data-driven understanding of your security operation, and you can recognize threats, qualify their effect on your bottom line, and create informed decisions to secure your business.
1. Keeps Companies Complaint
PII examination assists quickly in data discovery, ensuring your business’s consent with GPDR, HIPAA, and PCI needs. With the consistent converts in local and even global needs, PII examine ensures your companies does not experience possible risks and expenditures. Compliance with local, state, and local standards is critical to effective management. You could start into problems with the law. PII examination of digital arrangement also enables rapid indexing. It can assist in screening data that are not required to monitor companies from getting too much data.
2. Enables Better Data Discovery
Ensuring your data undergoes PII examination assists your management in determining the data you can find on your servers. After recognizing data, your management can assure the data owners their data is monitored and secure from dealing. Effective data discovery also enhances user beliefs and your management’s overall distinction. A PII assessment helps you not only improve discovery but also reduce issues. The outcomes are an additional boost in trust from your users.
3. Avoid Future Security Errors
Typically, PII examination avoids future PII escapes. Without it, you are seeing a crowd of security risks that could impact your relationship with your user—or with the law. PII examine can recognize both encrypted and unencrypted data, when you can pinpoint unencrypted data, you can go back in and encode it to ensure that it’s secure from escapes. For instance, when personal user data is port unprotected, it’s more probable that hackers will obtain access to that data. If someone’s social security number, for instance, is unencrypted, this could guide to recognizing theft.

4. Minimizes Data Tracking
Data tracking maximizes the risk of sensitive data being in the wrong hands. But with PII examination allowed, sensitive data gets better security, making it solid for users’ data to be transformed from one business to another attend on the transformation happens without acquiring consumer permission. PII examination can also minimize data theft. If your management operates a PII examination, it assists and determines the proper storage of PII. It also helps to recognize the continuous design regarding how your group stores, uses, and saves data within your interior CRM Software.
5. Actual-time Threat Detection
Consistently observing for irregularities and evaluating relevant data allows for real-time vulnerability identification, especially in fresh schemes such as zero-day threat enterprises. Opponents frequently manufacture and persist access in networks for extensive periods earlier being evaluated, where they bring out a range of malicious actions. Adaptive security accelerates vulnerability detection to the speed needed for businesses today.
6. Fewer Data Breaches
The increase from a network incursion to a data breach can take hours, days, or weeks. Regardless of how long it takes to access sensitive assets and delete them, data breaches are a risk that any company leader wishes to avoid. The quicker vulnerability detection and rapid times to resolution agreed by adaptive security limit the damage caused even when vulnerability actors organize to get past preventative handles.

7. Minimizes Attack Surface
An ignored advantage of adaptive security comes from the predictive level and how it minimizes your cyberattack surface. The attack surface is the total of all achievable points of inappropriate entry into your surroundings. Its attack surface involves software threats, unsecured worker endpoint tools and services with risky open ports.

8. Reliability
Another advantage of adaptive security is it doesn’t depend on a single stylish latest solution. The reliability here is that you can incorporate a security recached across many platforms and controls. To get the most form of adaptive protection, though, the latest analytics and machine learning needs to play a role because this is where the capabilities to study designs and natures and relate them to threat detection abilities come from.
9. Proactive Risk Management
By consistently observing and evaluating data for potential PII liability, adaptive detection systems allow proactive risk organizations to recognize threats and execute appropriate controls to avoid data breaches and privacy events before they happen.
10. Personalization And Adaptation
Adaptive PII detection solutions can be personalized and fine-tuned to meet the particular requirements of distinct industries, organizations, and use cases. They can adapt to rare data surroundings, business procedures, and compliance direction, ensuring optimal operation and efficiency.