Recent posts
I have an HP Compaq Presario with a built in microphone and my PC is using Windows Vista ultimate as an OS. Every now and then I need to make urgent calls to my business partners and most of them complain that my microphone volume drops really low after...
Read more
In a Neural Network there are two methods that we can train the network. One of method is Supervised Training. To do that Training we can use the Delta Rule. This is one of Example that I had found.
Can anybody explain me how to find the...
Read more
When I was searching about the Public Key Encryption I found this diagram that explains about the Public Key Encryption process.
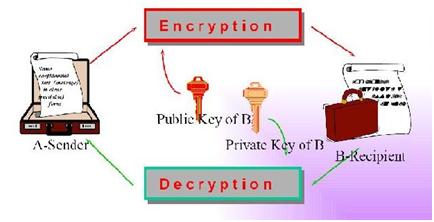
But I cannot understand what it will describe. So someone please describe me what is explaining from this diagram.
Read more
When we talk about the Information Systems Security, we use cipher algorithms to Encrypt or Decrypt data.
What is the basic work of the cipher and the basic concepts use in these ciphers.
- Caesar Cipher
- The Perfect Substitution
- The Vernam Cipher
- Block Cipher
- Stream Cipher
Read more
When we talking about the RAID (RedundantArray of Independent Disks), when learning about the RAID level 2 there was party called Hamming-party. What is mean by the Hamming-party and how it will help to make disk spindle rotation is synchronized?
Read more
From the Data Mining and Warehousing subject I found a process called clustering. Briefly describe me what is clustering and what the advantages of clustering. And also I need some details about these two different approaches to clustering:
· Partitioning methods
· Hierarchical methods
Read more
What is Thunderbolt technology in Mac? I came o know about this technology. How are Apple and Intel innovating on this integral part of computing systems?
Read more











