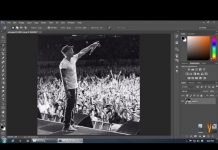
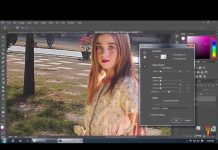
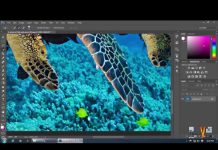
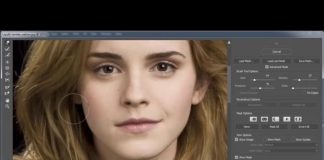
Tonal Selection With Channels In Photoshop
Latest Articles
Free cloud mining is coming! RICH Miner launches mobile mining, everyone can earn cryptocurrencies
RICH Miner officially launches a new mobile cloud mining application, subverting the traditional mining model! No need to buy mining machines, no technical experience required, just a mobile phone, global users can start the...
Rokid Max 2 Review: I Tried AR Glasses So I Could Watch Netflix in...
I’m not a tech geek. I don’t keep up with every new gadget launch. I fly a few times a year, watch many movies on my phone, and live in a small apartment where...
Top 10 Technology Trends For 2025
Pomperu -
With 2025 just around the corner, it is time to start thinking about what tech trends will be coming our way. Tech moves at a rapid pace. Some things may pop up next year...
Latest Blogs
Top 10 New Laptop Entrants That Shook The Public
L.rose -
The finest laptops are powerful enough to do your daily tasks, comfortable enough to use all day, and power-efficient enough to ensure you don't run out of battery power unexpectedly. Of course, all these...
10 Facts About The Dark Web
Before getting into knowing the facts, let’s have a brief about the Dark Web. The dark web is the data of the World Wide Web that is accessible only through special software, combinations, or...
Top 10 Latest Steam Cleaner Machines
Jaide -
While looking for a chemical-free way to clear and purify both durable and low grounds in your home, a steam cleaner is an excellent solution. With a spurt of superheated steam, this cleaning equipment...
Latest Tips
Top 10 Internet Monitoring Software
Internet monitoring software keeps a log of all internet activities. You can install this type of software on your computer remotely or by the administrator. An operating console controls this software. This type of...
Top 10 Best Partition Manager Software
A Hard Disk Drive is usually partitioned into various smaller drives for optimization. A partition manager helps make this process easier and more efficient. Here, let’s discuss the top 10 best partition manager software.
1....
Top 10 Best Online Music Production Software
Music production is the initial stage of any song. Music production can be done either in studios or at home using an online music production software. Here, let’s discuss the top 10 best online...