Detecting network Sniffers to collect data

Hi,
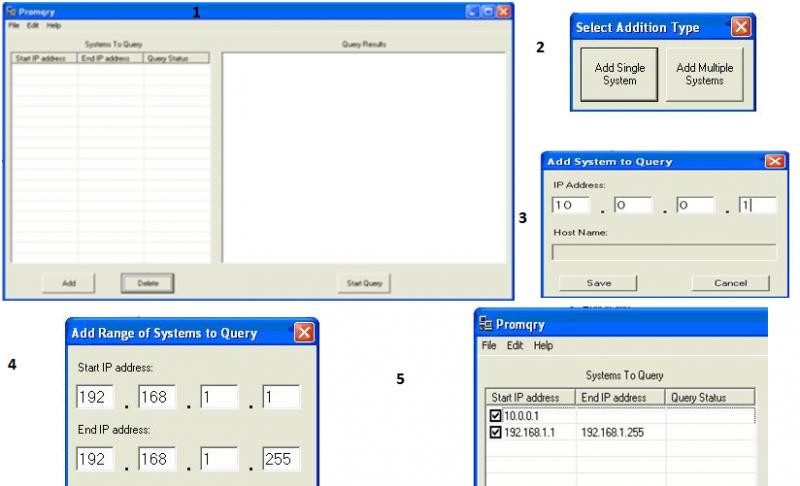
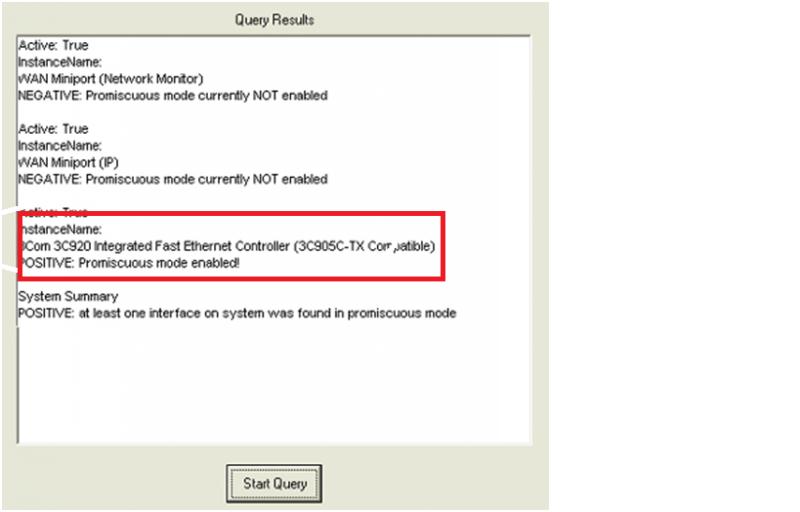
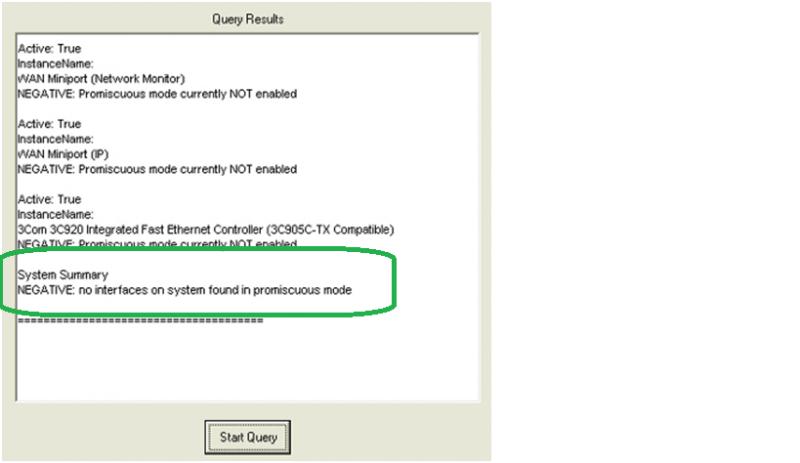
How one can detect network "sniffer"? Is it designed to collect data that is flowing across a network.?
The data can be useful for many purposes, including troubleshooting, network traffic analysis, and security purposes. However, the data can be used for illegitimate purposes, such as a network attack.
This type of data can also be used for illegitimate purposes, including data theft, unauthorized access on passwords, and networking mapping (reconnaissance).
This type of passive network attack can be difficult to detect.
Thanks.