Archive
Keep Your Computer Protected with Bsecure Online v6.16
Keep Your Computer Protected with Bsecure Online v6.16 Online connectivity is now-a-days one of the most powerful ways to connect. However, as the modern technology continues to spread, advantages bring disadvantages too. The viruses, malwares and others such things that can affect the function and performance of the computers as well as destroy the data are really disgusting. For children who need online access, there should be limitations or restrictions in order to be guided properly.Virtually Indestructible - Casio G'zOne Ravine (Verizon Wireless)

Check Out the New Dell XPS 15
Laptops are becoming quite the fad nowadays. Thus, Dell introduces Dell XPS 15 to replace those desktops. With its Intel core i5 processor and Nvidia GeForce GT 420M (that could still be enhanced before purchase), you won’t take a look on other laptops. The Dell XPS 15 also has a 15-inch 1080 pixel screen resolution that is HD webcam certified by Skype. Appearance The Dell XPS 15 has an aluminum casing which is similar to the Apple MacBook Pro. It has nice forward hinge design similar to the Inspiron line. The overall design, however, speaks corporate. With the size of 1.3X14.7X10.6 inches and a... Read moreAT&T USBConnect Velocity: 3 In 1 Portability
The AT&T USBConnect Velocity offers 3 In 1 features: Broadband modem, GPS and expandable Data storage. Paying for internet access or looking for WiFi hot spot, no worries. Anywhere in the world, you are connected through AT&T's or other foreign 3G, EDGE and WiFi networks.
ASUS U45Jc-A1: Maximum Portability in a Sleek Package
Fast and light with an impressive battery life packed in a sleek design makes ASUSU45Jc-A1’s maximum portability.
AMD Phenom II X2 560 Black Editions Compared to Intel Core CPUs
The processor is an integral part of a computer and is considered as its main processing unit. Without it, the computing device will definitely not run. Therefore choosing the best one for your computer will surely provide benefits. These days, processors are being innovated and improved. Some have simple specifications to various quads are now a days available in the market. Companies and manufacturers compete in terms of quality and performance of their product.A Look on the Apple iMac (21.5-Inch, 2010 Version)
You can see many computer producing companies claiming that they are producing the best laptops to replace all the desktops. Many companies claim that their product is better than the others because it performs a number of functions that can be delivered by various products; somewhat a complete packaged laptop. However, no matter what innovation other computer companies may add to their products, nothing will be able to beat the apple iMac, the king of all kings, because apple just stays on top.
A Detailed view of Dial Up Networking
- Dial up connection uses Public Switched Telephone network to access internet via telephone lines. It uses the modem to modulate and demodulate IP packets. In this, dial up connection sends signals through telephone lines.
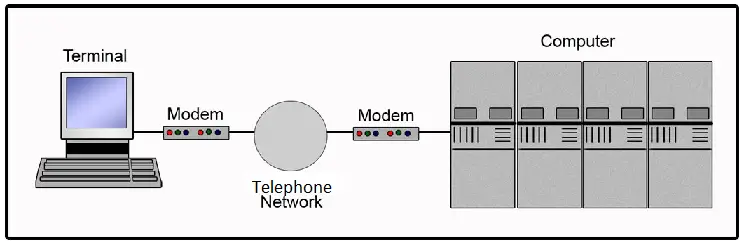
- The advantages of Dial up connection are that its cost is low, full time availability as it requires only a telephone line, modem and provides security also; and the disadvantage is that its speed is slow as compared to others and while using the dial up connection, the phone line is busy. ... Read more
Secure Socket Layer And Its Uses
- Today, applications like online banking, financial transactions during shopping using credit card and electronic stock credit, all require a secure connection. SSL fulfills these requirements by giving a secure connection. It is used to provide security at the level of Application layer.
- SSL builds a protected connection between two sockets, including 1) Parameter recognition between client and server; 2) Check the authentication for both client and server; 3) Secret communication; 4) Data reliability protection. SSL widely implemented HTTP connection. HTTPs mean a secure connection which is used by SSL.
Use of Cryptography in Security
As we know in today’s world, network security is a big issue. Here we will try to understand one type of network security solution i.e. Cryptography. Cryptography, invented since Greek times, means “Secret writing”. It is a skill to hide the message in such a way that it will become secure and protected to attacks.












