
While you are to install any new thing in your system, it will surely take your time. People also face a lot of confusions and questions switching continuously till the installation have completed successfully. Need to know the guidelines for Windows 7 Remote Admin Tools?
Know The Instructions For Windows 7 Remote Admin Tools Installation

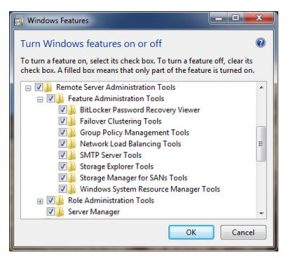
Depending upon the type of version, you have to use or install the Server Administration Tools offered by Microsoft. If you are using Win 7 then download the corresponding Windows 7 Remote Admin Toolspack from the link, where the instruction will also be provided.
Make sure that you have and using the Admin account. If you are using any other remote admin tools on your system, remove it before installing this new pack since only one copy can be possibly connected at a time in a computer. Simple steps, you need to open the downloaded package folder to unpack and start the RSA setup wizard. Accept the terms and conditions of the warranty carton and install by finishing the process.
Know The Instructions For Windows 7 Remote Admin Tools Installation

A RAT or Remote Administration Tool is a kind of application or programming that allows a user or operator to control a system as if they can access it physically. Though remote administration and desktop sharing have plenty of lawful uses, remote administration tool applications are often associated with malicious activity. Normally, malicious RAT applications are installed without authorization or without the user’s knowledge.
They often appear as payload of a Trojan horse and will always try to hide operation from the user and from a security application. A RAT application is controlled using a network connection. It can be the internet or local area network. These tools allow an operator to acquire the following capabilities:
- Screen or camera capture or image control
- File management – the operator can download, upload, and execute a program on the victim’s computer.
- Shell control – the operator can execute commands from the command prompt on the victim’s computer.
- Control the computer – the operator can turn off or turn on the victim’s computer even log off if this remote feature is supported.
- Manage registry – the operator can query, add, delete, and modify registry entries on the victim’s computer.
- Hardware Destroyer (overclocker) – the operator can damage the machine by overclocking its processor over its maximum capacity.













